As a business evolves its IT systems need to evolve with it. This has become even more apparent over the last few years as businesses of all sizes have had to become more flexible and adaptable to succeed. Unfortunately, some businesses don’t have the in-house resource or expertise to manage these changes and this is where bridging the gap and partnering with a Managed Service Provider (MSP) to oversee all your IT requirements comes in.
In this article we look at the benefits of partnering with a Managed IT Services Provider.
Minimise Downtime
IT downtime can have a direct impact on your bottom line and ongoing business operations. Servers can fail, computers can malfunction, or system attacks can take out your network and data. An in-house team may not have the experience to resolve these issues effectively, or the resource to respond to these swiftly. However, an MSP can help your business adopt a proactive approach to your IT infrastructure. For example, we offer a professional support package which includes proactive monitoring of every workstation (laptop and desktop), as well as servers. This package monitors connectivity, disk space, security, backup failures and will also identify and fix any issues before they impact on your business. An MSP also has the resource to respond quickly to these threats and can help you put a disaster recovery plan in place to help mitigate the impact of any downtime.
A Team of Experts
Your company may have an individual or a team in place to manage your IT and who are familiar with your existing systems. However, they may not have the necessary expertise or skills to operate new or updated systems and take on new responsibilities. An MSP will give you access to a team of diverse and knowledgeable experts who possess specialised skills and can provide extra resource to support a business’s current team or fill any gaps in their expertise, whilst also helping them to keep up to date with the latest technology trends and information.
Access to the Latest Technology
Technology is constantly evolving, and it can be difficult to discern what type of equipment or software is right for your business. Companies can make the mistake of investing in the wrong infrastructure or lack the expertise to manage it. An MSP will keep you updated on the latest industry trends and technologies and advise on which software is worth investing in. They will also take responsibility for the maintenance and upgrades of the systems involved.
24/7 Managed IT Support
It is essential for IT systems to be monitored constantly to prevent issues from occurring. An MSP will typically run a help desk 24 hours a day, seven days a week, meaning support is always available when customer’s need it.
Security
As cyber-attacks increase in frequency and sophistication, IT teams can struggle to deal with them. An MSP will have a team of experts with access to the latest tools and techniques to keep your business protected from data loss, hacking etc.
Acting as a trusted IT solutions partner to our clients; we provide reliable managed IT and advanced technology solutions. Our team of experts have their fingers on the pulse of the technology industry and changing business landscape and will ensure you have the most sophisticated and best suited solutions for your business.
If you are looking for a North East Managed Services Provider, look no further than Bowe Digital. To find out more about our services, please get in touch today.
Microsoft has announced that it will be increasing its prices for Microsoft 365, Dynamics 365 and Power Platform SKUs from 1st of March 2022, as well as introducing a New Commerce Experience (NCE).
The changes to the commercial pricing for Microsoft 365, which are the first substantive pricing updates since Office 365 launched a decade ago, reflect the shift towards hybrid working and support the advances in Office 365 and Microsoft 365.
The New Commerce Experience, the NCE ‘Per Seat’ model, is a licensing model which is based on the number of ‘seats’/people who use the software. The aim of this approach is to reduce licensing complexity and provide flexibility for future growth. NCE per Seat will be available for Microsoft 365, Dynamics 365, and Power Platform SKUs with terms of 1 month, 1 year or 3 years.
1 month subscription
- Benefits – Useful for seasonal businesses or those with uncertain workforce patterns, the 1-month commitment offers flexibility.
- Term – One full month with no pro-rata refunds.
- Price – 20% higher than the 12 month subscription.
- Seat changes – Seats can be increased at any time. You cannot decrease the number of licenses/reduce your seat count during the subscription term.
12 month subscription
- Benefits – The 12-month term commitment allows you to secure a fixed cost for one year.
- Term – Twelve months with no pro-rata refunds.
- Price – In line with current pricing.
- Seat changes – Seats can be increased at any time. You cannot decrease the number of licenses/reduce your seat count during the subscription term.
36 month subscription
- Benefits – The 36-month term commitment allows you to secure a fixed cost for three years.
- Term – Thirty-six months with no pro-rata refunds.
- Price – In line with current pricing.
- Seat changes – Seats can be increased at any time. You cannot decrease the number of licenses/reduce your seat count during the subscription term.
Please note, Microsoft will not provide pro-rata refunds for the early termination of any subscription in NCE Per Seat outside of an initial 72-hour cancellation window.
What does this mean for you?
If you are a Microsoft 365 customer of Bowe Digital, a member of our team will be in touch with you to discuss the changes in more detail. In the meantime, if you have any concerns or questions about the changes, please contact us.
Cyber attacks can be extremely damaging to businesses, not only by disrupting day-to-day operations, but they can also be harmful to a company’s reputation, particularly if they result in compromising client data. It is crucial that your business has reliable cyber security measures in place, from a provider you can trust, to combat cyber threats and protect your business’s operations and reputation.
What is a Cyber Attack?
A cyber attack is an assault, launched by cybercriminals, that can disable computers, steal data, or use a breached computer as a launch point for other attacks. Cyber attacks can be launched in a variety of different ways, including malware, phishing, ransomware, and denial of service, among other methods.
Almost 40% of businesses had a cyber security breach or attack in the last 12 months, as reported by The UK Government’s Cyber Security Breaches Survey 2021. Most cyber attacks are permitted by human error, by system users choosing a password that is easy to figure out or not changing the default password on devices such as routers.
What is Cyber Security?
Cyber security is the application of technologies, processes, and controls to protect systems, networks, programs, devices, and data from cyber attacks. It reduces the risks of cyber attacks and protects against the unauthorised exploitation of systems, networks and technologies.
The most effective cyber security is made up of several layers of protection, such as:
- Using multiple strong passwords
- Implementing two factor authentication
- Installing anti-virus software
- Developing a backup and disaster recovery plan
- Ensuring all employees are trained in your business’s cyber security protocol
- Ensuring all software updates and patches are completed regularly
How can we help?
Based in the North East, we provide a range of IT services and transformative technology solutions which includes cyber security, as well as cloud solutions, hardware, networking, software and IT support services, to help your business increase productivity, improve performance, enhance connectivity, and reinforce security.
We safeguard your business and mitigate the risk of cyber threats with our robust and reliable cyber security solutions. This includes Datto SIRIS Disaster Recovery and Back-Up systems, and Webroot Antivirus Protection software. Datto SIRIS is a robust business continuity solution that brings together state of the art hardware with a secure cloud storage capability. Webroot’s Antivirus Protection protects against threats across email, browsers, files, URLs, ads, apps, and more in real time. It enables endpoint management anywhere, anytime, online.
We also offer Datto SaaS cloud backup for Microsoft 365 to provide you with peace of mind and mitigate the impact of a cyber attack. Datto SaaS, a leading cloud-to-cloud backup product, protects the data you entrust to the cloud. It offers an all-in-one backup, restore and export solution that covers Exchange Online, OneDrive and SharePoint Online.
In addition, we can support you in achieving your Cyber Essentials certification from the National Cyber Security Centre (NCSC), part of Government Communications Head Quarters (GCHQ).
You can have peace of mind with Bowe Digital’s technical experts and cyber security solutions protecting your business.
Get in touch with our specialists today to find out more about how we can protect your organisation against cybercriminals here.
Our mission is to enable our customers to realise their ambitions through the provision and application of advanced technology. We offer a wide range of innovative and transformative IT solutions across the North-East to help your business increase productivity, improve performance, enhance connectivity, and reinforce security. This includes IT support, cyber security solutions, software, cloud systems and more.
Below are just some of the many services and software we offer.
IT Solutions
We understand IT systems are crucial to the running of your business, so we offer two IT support packages based on your needs. Both our IT Support Standard and IT Support Professional offer an audit of your network and infrastructure, phone and remote dial in support, webinar and seminar invitations, managed updates for servers and computers and more. Our Professional IT Support package offers onsite support, as well as Webroot antivirus protection, quarterly reports and proactive IT monitoring, to keep your systems running smoothly.
Microsoft 365 Installation and Migration
We offer Microsoft 365 Installation and Migration, which allows you to share and create anywhere, on any device, by combining best-in-class apps like Excel and Outlook with powerful cloud services like OneDrive and Microsoft Teams.
Cyber Security
We can help you to protect the data you entrust to the cloud with Datto SaaS Protection for Office 365, a leading cloud-to-cloud backup product offering an all-in-one backup, restore and export solution that covers Exchange Online, OneDrive and SharePoint Online. We work in partnership with Datto to provide business continuity and disaster recovery solutions at a price affordable to SMEs, so you can protect your business whatever the size.
We also offer antivirus protection with Webroot, which provides endpoint protection that secures your business by harnessing machine learning, classifying, and scoring 95% of the internet three times a day, to keep your information safe.
Certifications
Protect your organisation against cyber-attacks and demonstrate your commitment to cyber security with advice and certification from the National Cyber Security Centre (NCSC), part of Government Communications Head Quarters (GCHQ). We can support you in achieving your certification.
VoIP
Also known as Hosted Telephony, VoIP refers to the idea of making calls over the internet as data rather than a traditional analogue phone system, which can significantly reduce call costs particularly when making international calls.
VoIP allows users to make international calls without the expensive rates non-VoIP users receive. With calls moving as data, a business using Packnet would be able to get free calls between employees in different countries. Calling VoIP-to-VoIP is becoming the more cost-effective option with straightforward charges as VoIP users do not have to rely on a fixed monthly fee.
Training
Training is an integral part of the service which we offer. We include training in all new business proposals to ensure that the end user feels comfortable using their chosen product to its full potential. We also provide expert training on all our software products including BaPS and Microsoft.
Hardware
We have extensive knowledge and a breadth of experience to draw on when choosing the best hardware for your business. We can also advise you on which new hardware will work best with your current equipment, saving you time and money.
To find out more about how we can help your business with our extensive IT solutions and services, contact us here.
Your IT systems are crucial to the running of your business, so it makes sense to ensure those systems run smoothly with good IT support.
When it comes to IT, reactive support resolves issues once they have occurred. Proactive support aims to prevent any issues from occurring or escalating.
For Bowe Digital, this means that even when our clients don’t call upon us, our proactive monitoring software is checking the performance of their system. The software monitors every workstation, whether a laptop or a desktop, and if it spots a fault, it fixes it. If it can’t, it raises a ticket which is picked up and actioned by one of our engineers within 30 minutes for business-critical issues or within one hour for non-business-critical issues.
Our proactive monitoring software tracks key areas such as connectivity, disk space, security, backup failures and more.
Our proactive IT support isn’t just limited to hardware. Cyber security threats constantly pose a risk to businesses, therefore proactive support is just as critical as reactive support. That is why, as part of our Professional IT support package we offer our clients Webroot. Webroot’s Business Antivirus Protection protects against threats across email, browsers, files, URLs, ads, apps, and more, in real time. It enables endpoint management anywhere, anytime, online. Webroot offers protection utilising machine learning which classifies and scores 95% of the internet 3 times per day. This gives our customers peace of mind that their systems are safe.
What are the benefits of proactive IT support?
Proactive IT support ensures your systems are performing optimally at all times. As our proactive monitoring software is always analysing the performance of our customer’s system, any faults are detected immediately. This means that areas which could become an issue are resolved before our customers feel any impact, often saving valuable time and mitigating the financial impact of any downtime or outages.
We also take a proactive approach to the service we provide our customers. Committed to developing long-term relationships with our customers we take the time to truly understand their objectives, processes, and ambitions. In addition, our team of technical engineers have their fingers on the pulse of the technology industry. These factors allow us to anticipate our customers’ needs and review and refine the services offered, all to ensure they are receiving the best suited solution to meet their requirements.
As a leading IT support company, Bowe Digital recognises that all businesses are different and therefore we offer a choice of IT support. We have our IT Support Standard, and our IT Support Professional package which includes proactive IT monitoring.
For IT support in Newcastle upon Tyne, or the wider North East area, contact us.
One of the downsides of being in a remote region in the world like the Australian outback or even in some rural villages is the slow speeds of internet where fibre hasn’t quite reached yet or isn’t economically viable to do so.
Elon Musk and Space X looks to solve all these issues with satellite internet constellation called Starlink.
What is Starlink?
The Starlink constellation will consist of thousands of small satellites in low Earth orbit, working in unison with ground transceivers.
The satellites can be used by you and me, military or even specialist research, allowing faster connections all over the world and in some of the most inhabitable environments where internet signal could prove to be a life saver. The cost of the decade-long project to design, build, and deploy the constellation was estimated by SpaceX in May 2018 to be at least US$10 billion.
As of September 2020, SpaceX was launching up to 60 satellites at a time, aiming to deploy 1,584 of the 260 kg (570 lb) spacecraft to provide near-global service by late 2021 or 2022.
Last month Space X confirmed Starlink is now available in parts of Wales, Scotland, Northern Ireland and Northern England,” which is in addition to existing service areas across Southern England.
As more and more satellites are launched, the areas which are currently hit, and miss will receive better connection and better signal.
How many satellites will Space X launch?
ITs reported that by 2024, there might be as many as 4,425 in operation, exploding to 12,000 around 2026.
How much does this space age internet cost then?
Customers typically pay £89 per month for the service itself, plus £54 for shipping and £439 for the kit (dish, router etc.). It may not be the cheapest but if you are suffering from exceptionally poor internet, it may be worth considering.
How fast is fast?
During beta, users can expect to see data speeds vary from 50Mb/s to 150Mb/s over the next several months as Starlink system is enhanced. There will also be brief periods of no connectivity at all, which is unfortunate but that should only be until a satellite becomes in range in low earth orbit.
As Space X launch more satellites, install more ground stations, and improve the networking software, data speed, latency and uptime will improve dramatically.
So, there you have it. Do you suffer from extremely poor broadband in a rural area? Would you pay £89 per month? Let us know in the comments.
What is Multi-factor Authentication (MFA)?
Multi-factor Authentication (MFA) is a security system in which to gain access to a specific resource you need to provide two or more forms of identification. Some examples of this may be entering your password in addition to either a pin code sent to your mobile device, an authentication app, a fingerprint or a security key.
The majority of security breaches are due to insecure passwords. MFA helps prevent this as with a username and password alone, an attacker will not be able to gain access to a secure system or resource. This is because although they may have compromised the username and password, they still lack the second factor required to gain access.
So why implement Multi-factor Authentication (MFA)?
- According to Microsoft, when you implement MFA your accounts are up to 99.9% less likely to be compromised
- Implementing MFA can be low cost, or even free, depending which service(s) you use
- MFA can give you peace of mind that your data is secure when being accessed from locations other than the office
- MFA is generally very easy to use
- Small businesses are increasingly being targeted by cyber criminals. MFA makes it much harder for them and is easily rolled out
- Users are already becoming accustomed to using MFA for things like online banking
MFA is highly recommended by IT Security professionals:
- Alex Weinert, Microsoft’s Group Program Manager for Identity Security and Protection says, “Your password (rules) don’t matter, but MFA does. Go turn on MFA if you haven’t.”
- Symantec have said that 80% of security breaches could be prevented by using MFA
- The National Centre for Cyber Security (NCSC) in the UK recommend the use of MFA
- We at Bowe Digital use MFA in order to access Microsoft 365, Webroot, our RMM service and more
In conclusion, implementing MFA is definitely a step you should take in order to protect your business. The benefits of implementing MFA outweigh the drawbacks and it is an easy way to improve your security.
Contact us today for advice on how you can enforce MFA and protect your company.
Due to the current Covid-19 pandemic, many of us are adjusting to a new normal of working from home. Whilst there are benefits to this, it can present a unique set of new challenges. One such challenge is how to effectively communicate and collaborate with our colleagues without being in the same office.
The good news is there is a huge range of software designed for this purpose to choose from. In this article, we will cover the four most prominent on the market today and examine the advantages and limitations of these.
1. Microsoft Teams
Part of the Microsoft 365 suite, Microsoft Teams is a communication and collaboration platform which replaces Skype for Business. Microsoft Teams combines workplace chat, video meetings, file storage and collaboration on files.
Advantages:
- Comes with Office 365 at no additional cost (depending on license)
- Instant messaging eliminates the need for long email chains
- Video calls with multiple colleagues at once
- Easy to implement and use
- File sharing and collaboration
- App integration
Limitations/Issues:
- Requires an Office 365 subscription
- Team set up and permissions can be complex
2. Zoom
Zoom is a cloud-based online meetings platform which has recently gained a lot of attention due to its ease of use and media coverage. Video conferencing, chat and business telephony services are their main offerings.
Advantages:
- Use of the video conferencing platform is completely free for up to 40 minutes with a maximum of 100 participants
- Sign up is not required for participants by default
- Easy to use and works on most devices
- Up to 1000 video participants on business plans with 49 video feeds on screen
- Screen sharing and annotation
- File sharing
Limitations/Issues:
- Information security professionals have raised concerns about Zoom’s data security and privacy practises
- “Zoom-bombing” – where unwanted users can enter a meeting and disrupt it if they find the meeting link
- Audio and video quality can deteriorate when large numbers of participants join a meeting
3. Slack
Slack is an instant messaging application to which has been around since 2013. It is relatively similar to Microsoft Teams in terms of its offerings.
Advantages:
- Ability to create channels to divide your teams and dedicate people to focused discussions and work
- Channels allow you to host video calls, chat separately within your own team and host virtual meetings
- File sharing between teams for collaboration
- Easy to use, simple design
- Automated actions and reminders
Limitations/issues:
- High volume of “urgent” messages
- Can be difficult to retrieve important information from a Slack chat
- Private channels cannot be changed to public if needed
- Can become expensive for larger companies
4. Google Meet
Available as a part of G Suite, Google Meet is Google’s enterprise video conferencing software. You can have a maximum of 250 participants on the enterprise license.
Advantages:
- Comes with G-suite at no extra cost
- Works in-browser on Google Chrome, Firefox, Microsoft Edge and Safari without installing any additional software or plugins
- Integrates with other meeting solutions
- Guests can join using a dial-in phone number in case of not having internet access
Limitations/Issues:
- Dashboard is not as clean as in some other meeting software
- No free option (you must have a G suite subscription to host meetings)
- No end-to-end encryption of video meetings
What is Office 365?
Office 365 is a cloud based subscription service from Microsoft which gives users access to a suite of productivity software including (but not limited to) Word, Excel, Outlook, Powerpoint, Access, Teams and Skype. There are a number of subscription options available depending on your needs, from plans which include only the online version of office applications to plans which include desktop office applications plus additional services like OneDrive and Sharepoint.
So why should you switch?
Here are 10 reasons to switch to Office 365.
1. Access your Office products from any location at any time
Office 365 is cloud based, so you can securely access your office products from anywhere that has an internet connection as long as you have a compatible device. You just need to browse to https://portal.office.com and log in.
2. No servers or maintenance required
Because Office 365 is cloud-based, there is no requirement to have your own local server (although Office 365 can integrate with an existing on-premise solution if desired). This means you can make big savings on maintenance costs associated with having an on-premise server.
3. Scaleability
Office 365 subscriptions are designed to be scalable and flexible. Licensing works on a pay-as-you-go basis so you can add and remove users and licenses as required. Because there are no minimum license requirements, you can buy as many or as few licenses as you need at the time, meaning you will never over pay or be forced to buy licenses that you do not need.
4. No downtime for updates
With Office 365, you will always have access to the latest version of your Office products. Because you are using Microsoft’s servers, there is no local server downtime required for updates. Office will download and install these updates in the background automatically – this means no disruption to your business critical services.
5. 10 Installs per user licence
With Office 365, every user is given up to 10 Office installs. 5 of these can be on a desktop and 5 on a mobile device. This means you can have Office installed on every device you are likely to use at no extra cost other than your monthly subscription.
6. Security
Office 365 has some of the best security measures in the industry. Office 365 complies with ISO 27001, HIPAA and FISMA. Data Loss Prevention Policies, message encryption, Advanced Threat Analytics (ATA) and Mobile Device Management (MDM) are all built in as standard to help keep your corporate data secure.
7. Cloud storage
OneDrive for Business provides each licensed user with 1TB of cloud storage. This is great because it enables users to securely store and access their important data from anywhere.
8. Moves IT costs from large one off costs to smaller monthly payments
Because Office 365 is subscription based, this eliminates large annual costs for Office products and replaces them with a smaller monthly cost. This monthly cost can be really helpful from a cash flow perspective and it also gives you the flexibility to add and remove services as required to help manage costs.
9. Support
Microsoft provide full support for all Office 365 products. Support for critical issues is available within 1 hour, 24 hours a day, 7 days a week.
10. Easy migration
Microsoft provide many different ways to migrate from your existing service over to Office 365. They provide step-by-step guidance on how to do this for each scenario on their website and detailed information on the potential impact of each method. If you choose to migrate over to Office 365 with us, we will take care of every step of the process and work to ensure minimal disruption to your business.
For more information on Office 365 and how it can benefit your business, click here to contact us today!
Phishing is a form of cyber attack where attackers attempt to trick users into doing ‘the wrong thing’, such as clicking a bad link that will download malware, or direct you to a website which may look identical to the original website, but may harbour spyware or be designed to collect your personal or financial information. In 2018 alone, phishing was responsible for $48,241,748 (£37,232,981.11) in losses.
Phishing can be conducted via a text message, social media, or by phone, but the term ‘phishing’ is mainly used to describe attacks that arrive by email. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive. Attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money.
Phishing emails can hit an organisation of any size and type. You might get caught up in a mass campaign (where the attacker is just looking to collect some new passwords or make some easy money), or it could be the first step in a targeted attack against your company, where the aim could be something much more specific, like the theft of sensitive data. In a targeted campaign, the attacker may use information about your employees or company to make their messages even more persuasive and realistic. This is usually referred to as spear phishing.
What does a Phishing email look like?

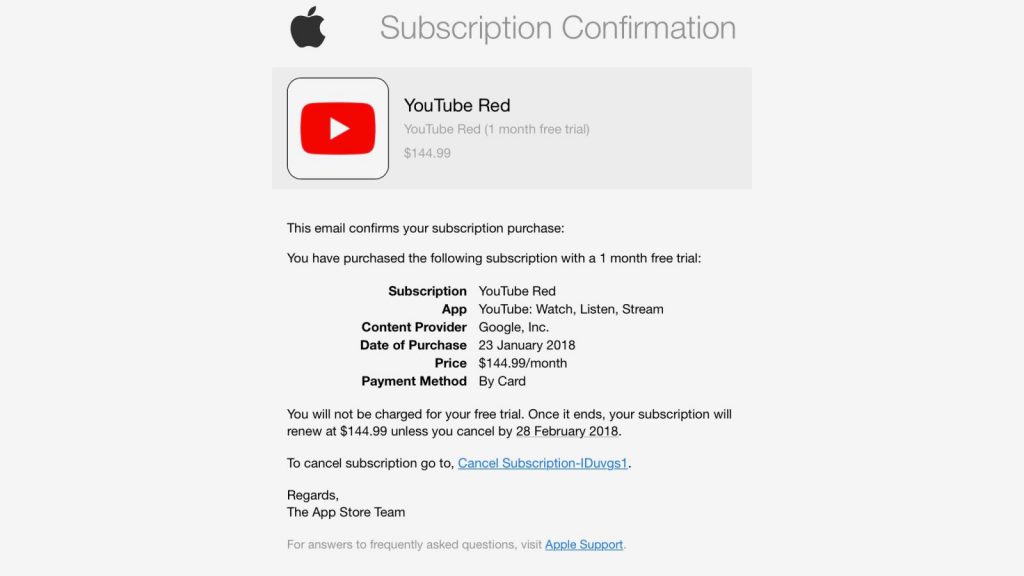
In this example above, we can see an email purporting to be from OneDrive, advising that there is a file which has been sent through to the user. Clicking the link in this email will result in malware being installed on your system. This is a common method of phishing where the attacker creates a message which would not look out of place amongst your normal work emails.
In this example above, we can see that an attacker has sent out an email attempting to get users to click the link and enter their Apple ID credentials. This may look convincing upon first glance, but as we look into it further, we can see that it is clearly not a genuine email. The combination of a non-apple email address being used to deliver the message, a generic and non-personalised greeting and the link pointing to a destination which has nothing to do with Apple are clear giveaways.
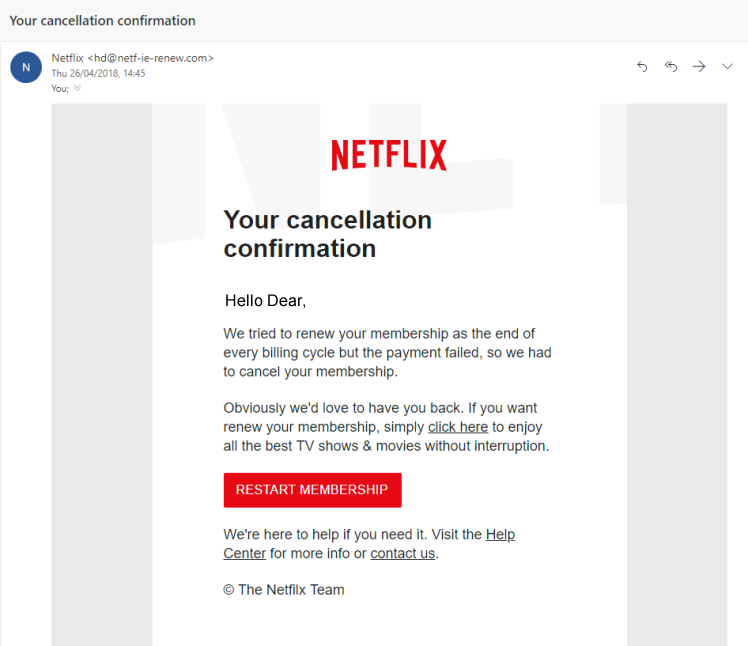
This example is one of the most common variants of a phishing email. On the surface, it looks pretty convincing – the branding is correct, the sign off seems correct and the look of the email seems legitimate apart from the recipient’s name. The only way you would be able to tell that this is not a legitimate email is to check the link in the email by hovering over it. In this case, it brings you to a false logon screen which is designed to steal your password. Another giveaway can be the email address that the message has originated from. Unless it is an @netflix.com (NOT @mailer.netflix.com or similar) email address, chances are it’s a phishing attempt.
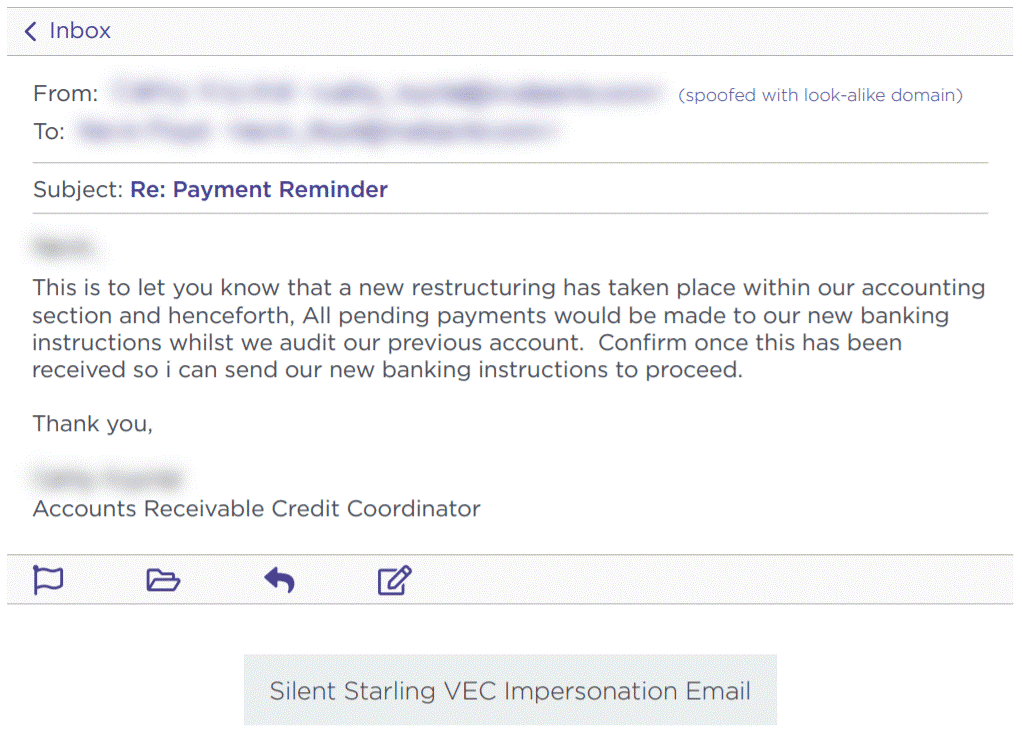
Another common type of phishing email is what is commonly known as ‘change of bank details fraud’ or ‘invoice fraud’. This involves a fraudster posing as a member of the accounts department of a supplier. The fraudster creates a convincing looking email and advises that their bank details have changed with the aim of getting you to make payments to the new account.
In order to avoid scams such as this, it is essential that you work on a basis of distrust when it comes to financial matters. If you are contacted out of the blue by a supplier to advise that their bank details have changed, call the customer on their official number (not the number in the email) and confirm this. If you receive an invoice that doesn’t seem quite right or that comes from a different email address, call the customer and check. It is better to be overly cautious than reckless – especially when bank details are involved.
So how can we avoid becoming a victim of these sorts of attacks?
Firstly, we suggest treating every email with a degree of suspicion. Think about the following:
- Is the sender’s email address correct? Often attackers use similar email addresses to legitimate senders so it is best to check this very carefully
- Were you expecting this message?
- Are there any ‘red flags’ such as spelling mistakes, incorrect information or suspicious attachments?
- Is there a request for payment or for you to sign in using your password?
- Does the message have a threatening tone? For example, does it advise that unless you take action immediately there will be severe consequences?
- Do you use the product which is mentioned?
- Is the email from someone you know and communicate with regularly?
When in doubt, it is always better to be safe than sorry. If the email purports to be from someone you know, call them and check that it is a legitimate message. If it appears to be from your bank or a government department, call them on the correct number and confirm (NOT the number in the email you have received, but the number from their official website).
Follow us to keep updated with all the latest IT news, tips, tricks and best practices.
References:
https://www.ncsc.gov.uk/guidance/phishing
https://it.sheridancollege.ca/service-catalogue/security/images/phishing-samples/amazon-phish.jpg
https://resources.infosecinstitute.com/category/enterprise/phishing/#gref
https://heimdalsecurity.com/blog/vendor-email-compromise-vec/