Regardless of the sector you operate in or the size of your business, when your operations rely on technology and access to data, it is crucial that your systems are always available and performing as required. If you have a system failure, the impact on your business can be catastrophic and can extend beyond financial consequences.
What causes downtime?
A common cause of downtime is ransomware attacks, which utilise encryption to hold the victims’ data at ransom, for a sum decided by the attacker. In the first four months of 2021, the National Cyber Security Centre handled the same number of ransomware incidents as they did in the entirety of 2020, with as many as one in three businesses being subject to cyber breaches.
A large number of businesses believe they are unlikely to be a victim of these, however a recent article from IT Pro warns that small businesses are more likely to be a victim of ransomware attacks in 2022 as cyber criminals begin utilising campaigns less likely to draw direct action from law enforcement.
Another leading cause of downtime, and one not always considered by businesses, is human error. Tech Radar details a famous example of this with the outage at British Airways in 2017. This was caused by an IT technician switching off an uninterruptable power supply, grounding 200 flights and leaving 75,000 customers stranded (Financial Times). The risk of human error causing business disruption and outages can be mitigated with proper training, but this does not eliminate the chance of it happening.
With ransomware attacks and the possibility of human error, as well as other common causes of downtime such as outdated hardware and bugs in a server’s OS, it makes sense to consider investing in solutions.
The true cost of downtime
From halting production or business operations to financial losses, data breaches and reputational damage – the true cost of downtime can be extensive.
In 2021 a study from the Phonemon Institute found the average cost of a data breach in the UK was £3.5million. However, it is important to note that it’s not just the cost of not being operational for hours or days that impact a business. One of the biggest consequences and cost factors in downtime is data loss which can cause ongoing problems for businesses.
The loss of customer and employee data can erode trust in a business and raise questions around security and GDPR. This can lead to people being less likely to use the business in the future and may make prospective employees wary of joining the company. This can affect customer loyalty and the business’s reputation in the long-term.
There are a wide range of factors that affect how much an outage will cost your business, from the amount of data on critical business systems and how regularly the data is backed up to the number of employees and business turnover.
We used a downtime calculator to estimate the cost of downtime to a business with no disaster recovery and backup solutions in place. In addition, the business has:
Data on business-critical systems: 2,500 GB
Cloud back up frequency: 12 hours
Employees: 40
Average employee salary: £25,000 pa
Average employee overhead: £10,000
Annual turnover: £500,000
It is anticipated that this business would experience more than 81 hours of downtime, costing £59,284. If the recovery process failed, it would cost the business an additional £8,700 per recovery attempt.
If the business had a disaster recovery and backup solution in place, they could have saved approximately £58,848. Recovery costs could be reduced to £1,734, and the business could be operational within 36 minutes.
Disaster recovery and backup solutions
Investing in disaster recovery and backup solutions can protect your business against substantial losses because of downtime. We provide a wide range of disaster recovery and backup solutions which can help protect your business from the impact of downtime and facilitate a speedy recovery. This includes software such as Datto SaaS Protection for Office 365 and Datto Siris.
We also offer preventative solutions such as training and cyber security software as well as ongoing IT support. Our professional IT support aims to prevent any issues before they occur, by utilising proactive monitoring software to spot faults and fix them before they escalate.
In many instances a small monthly fee for a back up and recovery solution can save a business thousands of pounds and minimise time offline. The cost of getting the right solutions and policies, far outweighs the cost in downtime – making these solutions an investment for the long term.
Find out more about the solutions we offer here.
Cyber attacks can be extremely damaging to businesses, not only by disrupting day-to-day operations, but they can also be harmful to a company’s reputation, particularly if they result in compromising client data. It is crucial that your business has reliable cyber security measures in place, from a provider you can trust, to combat cyber threats and protect your business’s operations and reputation.
What is a Cyber Attack?
A cyber attack is an assault, launched by cybercriminals, that can disable computers, steal data, or use a breached computer as a launch point for other attacks. Cyber attacks can be launched in a variety of different ways, including malware, phishing, ransomware, and denial of service, among other methods.
Almost 40% of businesses had a cyber security breach or attack in the last 12 months, as reported by The UK Government’s Cyber Security Breaches Survey 2021. Most cyber attacks are permitted by human error, by system users choosing a password that is easy to figure out or not changing the default password on devices such as routers.
What is Cyber Security?
Cyber security is the application of technologies, processes, and controls to protect systems, networks, programs, devices, and data from cyber attacks. It reduces the risks of cyber attacks and protects against the unauthorised exploitation of systems, networks and technologies.
The most effective cyber security is made up of several layers of protection, such as:
- Using multiple strong passwords
- Implementing two factor authentication
- Installing anti-virus software
- Developing a backup and disaster recovery plan
- Ensuring all employees are trained in your business’s cyber security protocol
- Ensuring all software updates and patches are completed regularly
How can we help?
Based in the North East, we provide a range of IT services and transformative technology solutions which includes cyber security, as well as cloud solutions, hardware, networking, software and IT support services, to help your business increase productivity, improve performance, enhance connectivity, and reinforce security.
We safeguard your business and mitigate the risk of cyber threats with our robust and reliable cyber security solutions. This includes Datto SIRIS Disaster Recovery and Back-Up systems, and Webroot Antivirus Protection software. Datto SIRIS is a robust business continuity solution that brings together state of the art hardware with a secure cloud storage capability. Webroot’s Antivirus Protection protects against threats across email, browsers, files, URLs, ads, apps, and more in real time. It enables endpoint management anywhere, anytime, online.
We also offer Datto SaaS cloud backup for Microsoft 365 to provide you with peace of mind and mitigate the impact of a cyber attack. Datto SaaS, a leading cloud-to-cloud backup product, protects the data you entrust to the cloud. It offers an all-in-one backup, restore and export solution that covers Exchange Online, OneDrive and SharePoint Online.
In addition, we can support you in achieving your Cyber Essentials certification from the National Cyber Security Centre (NCSC), part of Government Communications Head Quarters (GCHQ).
You can have peace of mind with Bowe Digital’s technical experts and cyber security solutions protecting your business.
Get in touch with our specialists today to find out more about how we can protect your organisation against cybercriminals here.
Watch a cyber attack at our FREE event & ensure your business is cyber safe!
- Does your business truly understand what a cyber-attack looks like?
- Do you know what impact this could have on business downtime?
- Are you aware of the financial impact of this on your business?
- Would you know if you have been hacked?
- Do you know how to get your business back up and running?
In the UK there are 4,500 successful daily cyber-attacks on SMEs. If this happened to your business, would you be prepared?
Do you know what a ransomware attack looks like and what it would do to your business? This is just one of the different types of cyber-attack that could happen to your business at any time. It is more a case of “when” rather than “if” your business will be subject to a threat.
We work in partnership with Datto to provide business continuity and disaster recovery solutions at a price affordable to SMEs.
We would like to invite you to join us for Bite Online, our free webinar on Thursday 26th November 2020, between 2pm and 3pm. Experience a live demo of a ransomware attack, then listen to guest speakers from Datto talking about how to have your business back up and running in a matter of minutes.
All attendees will also get access to a Downtime Cost Calculator which can be used to get an understanding of what an outage could mean to your business.
#cybersecurity #wemakeithappen #boweforit
What is Multi-factor Authentication (MFA)?
Multi-factor Authentication (MFA) is a security system in which to gain access to a specific resource you need to provide two or more forms of identification. Some examples of this may be entering your password in addition to either a pin code sent to your mobile device, an authentication app, a fingerprint or a security key.
The majority of security breaches are due to insecure passwords. MFA helps prevent this as with a username and password alone, an attacker will not be able to gain access to a secure system or resource. This is because although they may have compromised the username and password, they still lack the second factor required to gain access.
So why implement Multi-factor Authentication (MFA)?
- According to Microsoft, when you implement MFA your accounts are up to 99.9% less likely to be compromised
- Implementing MFA can be low cost, or even free, depending which service(s) you use
- MFA can give you peace of mind that your data is secure when being accessed from locations other than the office
- MFA is generally very easy to use
- Small businesses are increasingly being targeted by cyber criminals. MFA makes it much harder for them and is easily rolled out
- Users are already becoming accustomed to using MFA for things like online banking
MFA is highly recommended by IT Security professionals:
- Alex Weinert, Microsoft’s Group Program Manager for Identity Security and Protection says, “Your password (rules) don’t matter, but MFA does. Go turn on MFA if you haven’t.”
- Symantec have said that 80% of security breaches could be prevented by using MFA
- The National Centre for Cyber Security (NCSC) in the UK recommend the use of MFA
- We at Bowe Digital use MFA in order to access Microsoft 365, Webroot, our RMM service and more
In conclusion, implementing MFA is definitely a step you should take in order to protect your business. The benefits of implementing MFA outweigh the drawbacks and it is an easy way to improve your security.
Contact us today for advice on how you can enforce MFA and protect your company.
Phishing is a form of cyber attack where attackers attempt to trick users into doing ‘the wrong thing’, such as clicking a bad link that will download malware, or direct you to a website which may look identical to the original website, but may harbour spyware or be designed to collect your personal or financial information. In 2018 alone, phishing was responsible for $48,241,748 (£37,232,981.11) in losses.
Phishing can be conducted via a text message, social media, or by phone, but the term ‘phishing’ is mainly used to describe attacks that arrive by email. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive. Attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money.
Phishing emails can hit an organisation of any size and type. You might get caught up in a mass campaign (where the attacker is just looking to collect some new passwords or make some easy money), or it could be the first step in a targeted attack against your company, where the aim could be something much more specific, like the theft of sensitive data. In a targeted campaign, the attacker may use information about your employees or company to make their messages even more persuasive and realistic. This is usually referred to as spear phishing.
What does a Phishing email look like?

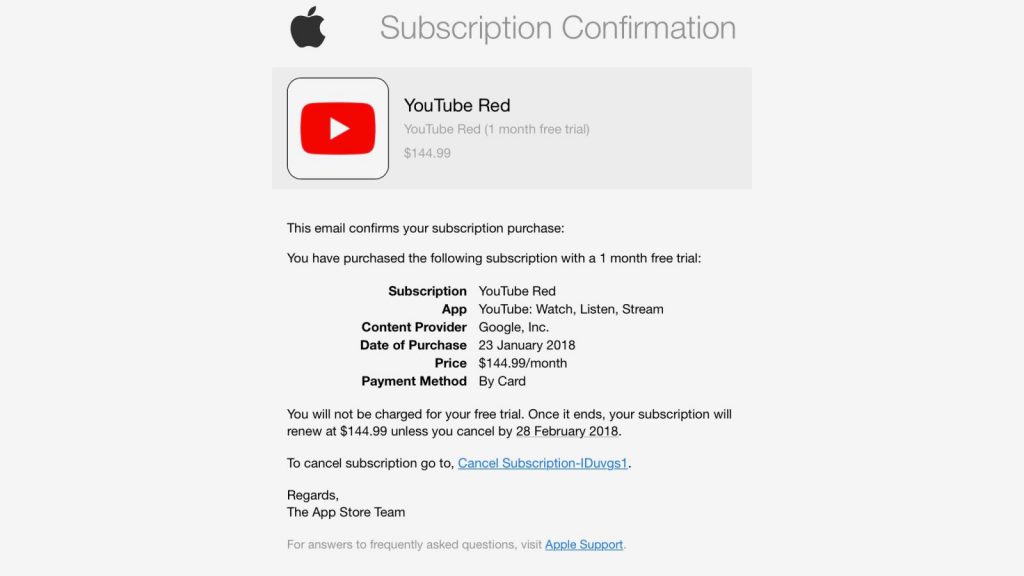
In this example above, we can see an email purporting to be from OneDrive, advising that there is a file which has been sent through to the user. Clicking the link in this email will result in malware being installed on your system. This is a common method of phishing where the attacker creates a message which would not look out of place amongst your normal work emails.
In this example above, we can see that an attacker has sent out an email attempting to get users to click the link and enter their Apple ID credentials. This may look convincing upon first glance, but as we look into it further, we can see that it is clearly not a genuine email. The combination of a non-apple email address being used to deliver the message, a generic and non-personalised greeting and the link pointing to a destination which has nothing to do with Apple are clear giveaways.
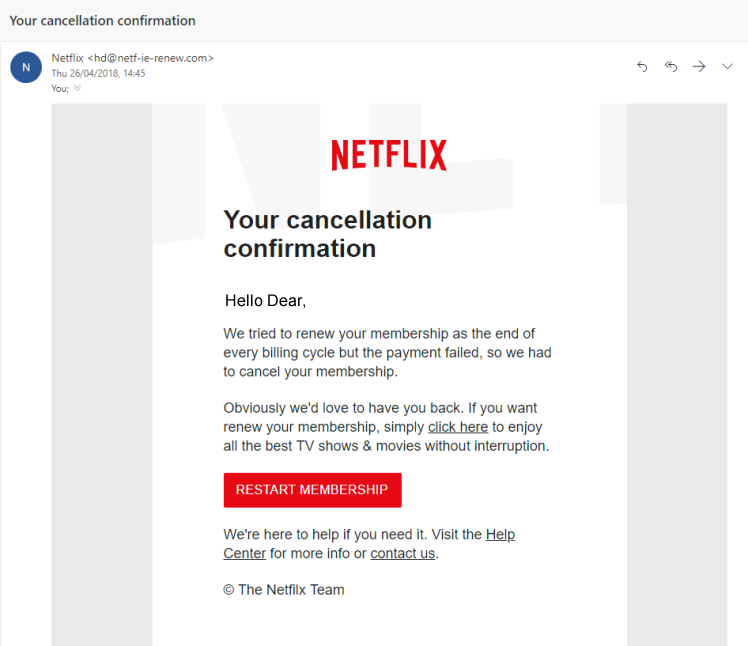
This example is one of the most common variants of a phishing email. On the surface, it looks pretty convincing – the branding is correct, the sign off seems correct and the look of the email seems legitimate apart from the recipient’s name. The only way you would be able to tell that this is not a legitimate email is to check the link in the email by hovering over it. In this case, it brings you to a false logon screen which is designed to steal your password. Another giveaway can be the email address that the message has originated from. Unless it is an @netflix.com (NOT @mailer.netflix.com or similar) email address, chances are it’s a phishing attempt.
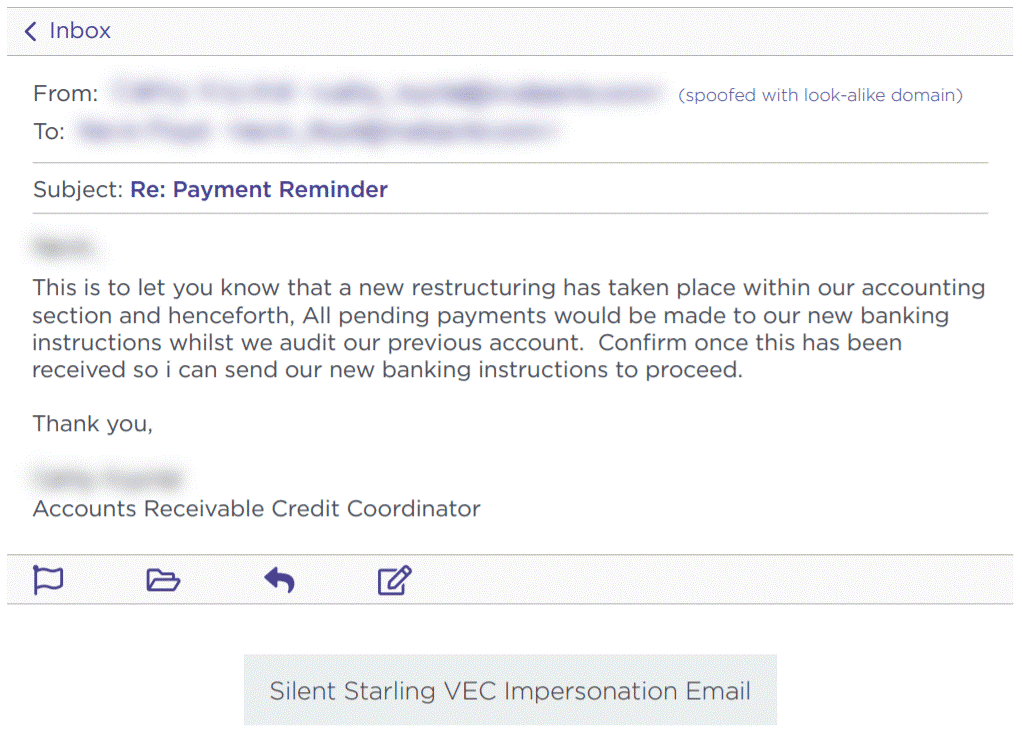
Another common type of phishing email is what is commonly known as ‘change of bank details fraud’ or ‘invoice fraud’. This involves a fraudster posing as a member of the accounts department of a supplier. The fraudster creates a convincing looking email and advises that their bank details have changed with the aim of getting you to make payments to the new account.
In order to avoid scams such as this, it is essential that you work on a basis of distrust when it comes to financial matters. If you are contacted out of the blue by a supplier to advise that their bank details have changed, call the customer on their official number (not the number in the email) and confirm this. If you receive an invoice that doesn’t seem quite right or that comes from a different email address, call the customer and check. It is better to be overly cautious than reckless – especially when bank details are involved.
So how can we avoid becoming a victim of these sorts of attacks?
Firstly, we suggest treating every email with a degree of suspicion. Think about the following:
- Is the sender’s email address correct? Often attackers use similar email addresses to legitimate senders so it is best to check this very carefully
- Were you expecting this message?
- Are there any ‘red flags’ such as spelling mistakes, incorrect information or suspicious attachments?
- Is there a request for payment or for you to sign in using your password?
- Does the message have a threatening tone? For example, does it advise that unless you take action immediately there will be severe consequences?
- Do you use the product which is mentioned?
- Is the email from someone you know and communicate with regularly?
When in doubt, it is always better to be safe than sorry. If the email purports to be from someone you know, call them and check that it is a legitimate message. If it appears to be from your bank or a government department, call them on the correct number and confirm (NOT the number in the email you have received, but the number from their official website).
Follow us to keep updated with all the latest IT news, tips, tricks and best practices.
References:
https://www.ncsc.gov.uk/guidance/phishing
https://it.sheridancollege.ca/service-catalogue/security/images/phishing-samples/amazon-phish.jpg
https://resources.infosecinstitute.com/category/enterprise/phishing/#gref
https://heimdalsecurity.com/blog/vendor-email-compromise-vec/
Header image credit – https://www.freepik.com
Can you really afford not to have a back-up plan?
We recently held our first customer seminar, over 2 sessions and had over 25 customers and prospects from businesses ranging from under 10 employees to over 200 employees’ businesses.

The event was looking at Datto and how this innovative cloud-based solution can benefit your business.
The event started with introductions and it was good to see lots of business cards being exchanged. As well as being dedicated to IT, we are very eager to always incorporate people interaction in our business.
Datto gave an overview of the dark web and where ransomware attacks come from. They ran a live ransomware attack and spun the system back up in 4 minutes. To recover from a cyber-attack with Datto cloud back up, it only takes as long as it takes the server to restart.
The biggest threat to your system isn’t cyber-attacks or fire, it’s human error!
So, having a system like Datto in place means your business can deal with interruptions and avoid downtime. We all know time is money so we really encourage you to get in touch and have a look at what a difference Datto can make.
If you didn’t get the chance to come along but would more information or a free demo give us a call on 0191 214 1750 or click here for more ways to contact us
Look out for more customer events coming up over the next few months.