Due to the current Covid-19 pandemic, many of us are adjusting to a new normal of working from home. Whilst there are benefits to this, it can present a unique set of new challenges. One such challenge is how to effectively communicate and collaborate with our colleagues without being in the same office.
The good news is there is a huge range of software designed for this purpose to choose from. In this article, we will cover the four most prominent on the market today and examine the advantages and limitations of these.
1. Microsoft Teams
Part of the Microsoft 365 suite, Microsoft Teams is a communication and collaboration platform which replaces Skype for Business. Microsoft Teams combines workplace chat, video meetings, file storage and collaboration on files.
Advantages:
- Comes with Office 365 at no additional cost (depending on license)
- Instant messaging eliminates the need for long email chains
- Video calls with multiple colleagues at once
- Easy to implement and use
- File sharing and collaboration
- App integration
Limitations/Issues:
- Requires an Office 365 subscription
- Team set up and permissions can be complex
2. Zoom
Zoom is a cloud-based online meetings platform which has recently gained a lot of attention due to its ease of use and media coverage. Video conferencing, chat and business telephony services are their main offerings.
Advantages:
- Use of the video conferencing platform is completely free for up to 40 minutes with a maximum of 100 participants
- Sign up is not required for participants by default
- Easy to use and works on most devices
- Up to 1000 video participants on business plans with 49 video feeds on screen
- Screen sharing and annotation
- File sharing
Limitations/Issues:
- Information security professionals have raised concerns about Zoom’s data security and privacy practises
- “Zoom-bombing” – where unwanted users can enter a meeting and disrupt it if they find the meeting link
- Audio and video quality can deteriorate when large numbers of participants join a meeting
3. Slack
Slack is an instant messaging application to which has been around since 2013. It is relatively similar to Microsoft Teams in terms of its offerings.
Advantages:
- Ability to create channels to divide your teams and dedicate people to focused discussions and work
- Channels allow you to host video calls, chat separately within your own team and host virtual meetings
- File sharing between teams for collaboration
- Easy to use, simple design
- Automated actions and reminders
Limitations/issues:
- High volume of “urgent” messages
- Can be difficult to retrieve important information from a Slack chat
- Private channels cannot be changed to public if needed
- Can become expensive for larger companies
4. Google Meet
Available as a part of G Suite, Google Meet is Google’s enterprise video conferencing software. You can have a maximum of 250 participants on the enterprise license.
Advantages:
- Comes with G-suite at no extra cost
- Works in-browser on Google Chrome, Firefox, Microsoft Edge and Safari without installing any additional software or plugins
- Integrates with other meeting solutions
- Guests can join using a dial-in phone number in case of not having internet access
Limitations/Issues:
- Dashboard is not as clean as in some other meeting software
- No free option (you must have a G suite subscription to host meetings)
- No end-to-end encryption of video meetings
What is Office 365?
Office 365 is a cloud based subscription service from Microsoft which gives users access to a suite of productivity software including (but not limited to) Word, Excel, Outlook, Powerpoint, Access, Teams and Skype. There are a number of subscription options available depending on your needs, from plans which include only the online version of office applications to plans which include desktop office applications plus additional services like OneDrive and Sharepoint.
So why should you switch?
Here are 10 reasons to switch to Office 365.
1. Access your Office products from any location at any time
Office 365 is cloud based, so you can securely access your office products from anywhere that has an internet connection as long as you have a compatible device. You just need to browse to https://portal.office.com and log in.
2. No servers or maintenance required
Because Office 365 is cloud-based, there is no requirement to have your own local server (although Office 365 can integrate with an existing on-premise solution if desired). This means you can make big savings on maintenance costs associated with having an on-premise server.
3. Scaleability
Office 365 subscriptions are designed to be scalable and flexible. Licensing works on a pay-as-you-go basis so you can add and remove users and licenses as required. Because there are no minimum license requirements, you can buy as many or as few licenses as you need at the time, meaning you will never over pay or be forced to buy licenses that you do not need.
4. No downtime for updates
With Office 365, you will always have access to the latest version of your Office products. Because you are using Microsoft’s servers, there is no local server downtime required for updates. Office will download and install these updates in the background automatically – this means no disruption to your business critical services.
5. 10 Installs per user licence
With Office 365, every user is given up to 10 Office installs. 5 of these can be on a desktop and 5 on a mobile device. This means you can have Office installed on every device you are likely to use at no extra cost other than your monthly subscription.
6. Security
Office 365 has some of the best security measures in the industry. Office 365 complies with ISO 27001, HIPAA and FISMA. Data Loss Prevention Policies, message encryption, Advanced Threat Analytics (ATA) and Mobile Device Management (MDM) are all built in as standard to help keep your corporate data secure.
7. Cloud storage
OneDrive for Business provides each licensed user with 1TB of cloud storage. This is great because it enables users to securely store and access their important data from anywhere.
8. Moves IT costs from large one off costs to smaller monthly payments
Because Office 365 is subscription based, this eliminates large annual costs for Office products and replaces them with a smaller monthly cost. This monthly cost can be really helpful from a cash flow perspective and it also gives you the flexibility to add and remove services as required to help manage costs.
9. Support
Microsoft provide full support for all Office 365 products. Support for critical issues is available within 1 hour, 24 hours a day, 7 days a week.
10. Easy migration
Microsoft provide many different ways to migrate from your existing service over to Office 365. They provide step-by-step guidance on how to do this for each scenario on their website and detailed information on the potential impact of each method. If you choose to migrate over to Office 365 with us, we will take care of every step of the process and work to ensure minimal disruption to your business.
For more information on Office 365 and how it can benefit your business, click here to contact us today!
Phishing is a form of cyber attack where attackers attempt to trick users into doing ‘the wrong thing’, such as clicking a bad link that will download malware, or direct you to a website which may look identical to the original website, but may harbour spyware or be designed to collect your personal or financial information. In 2018 alone, phishing was responsible for $48,241,748 (£37,232,981.11) in losses.
Phishing can be conducted via a text message, social media, or by phone, but the term ‘phishing’ is mainly used to describe attacks that arrive by email. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive. Attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money.
Phishing emails can hit an organisation of any size and type. You might get caught up in a mass campaign (where the attacker is just looking to collect some new passwords or make some easy money), or it could be the first step in a targeted attack against your company, where the aim could be something much more specific, like the theft of sensitive data. In a targeted campaign, the attacker may use information about your employees or company to make their messages even more persuasive and realistic. This is usually referred to as spear phishing.
What does a Phishing email look like?

In this example above, we can see an email purporting to be from OneDrive, advising that there is a file which has been sent through to the user. Clicking the link in this email will result in malware being installed on your system. This is a common method of phishing where the attacker creates a message which would not look out of place amongst your normal work emails.
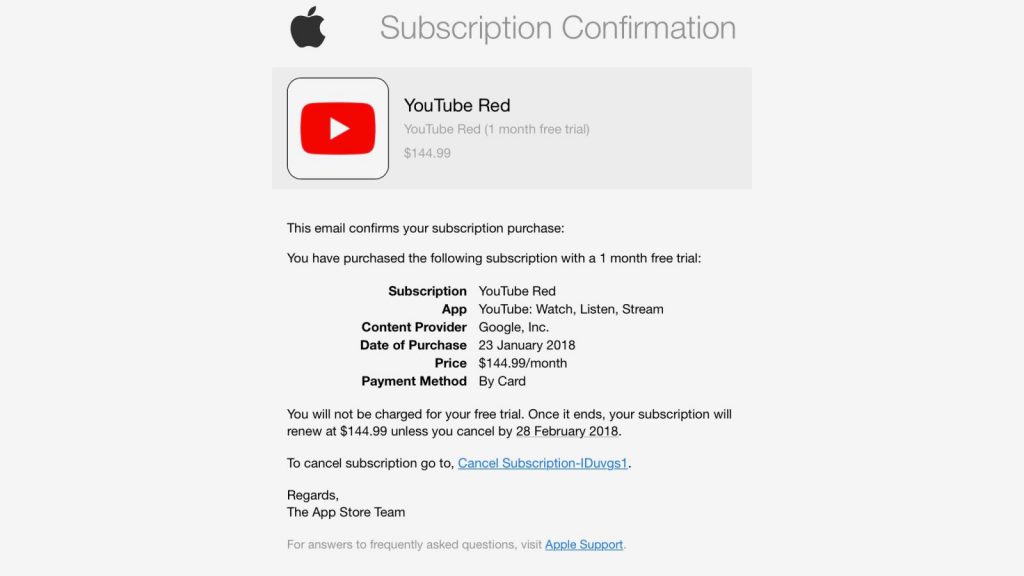
In this example above, we can see that an attacker has sent out an email attempting to get users to click the link and enter their Apple ID credentials. This may look convincing upon first glance, but as we look into it further, we can see that it is clearly not a genuine email. The combination of a non-apple email address being used to deliver the message, a generic and non-personalised greeting and the link pointing to a destination which has nothing to do with Apple are clear giveaways.
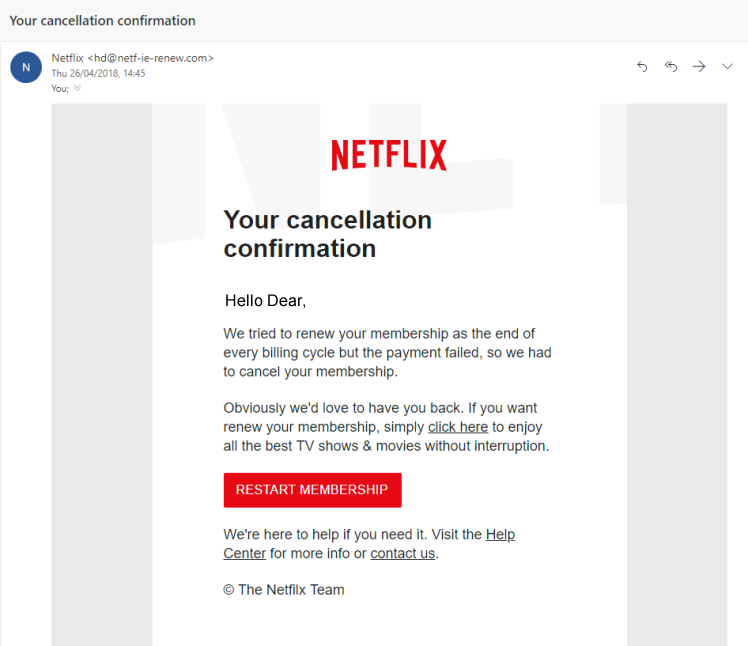
This example is one of the most common variants of a phishing email. On the surface, it looks pretty convincing – the branding is correct, the sign off seems correct and the look of the email seems legitimate apart from the recipient’s name. The only way you would be able to tell that this is not a legitimate email is to check the link in the email by hovering over it. In this case, it brings you to a false logon screen which is designed to steal your password. Another giveaway can be the email address that the message has originated from. Unless it is an @netflix.com (NOT @mailer.netflix.com or similar) email address, chances are it’s a phishing attempt.
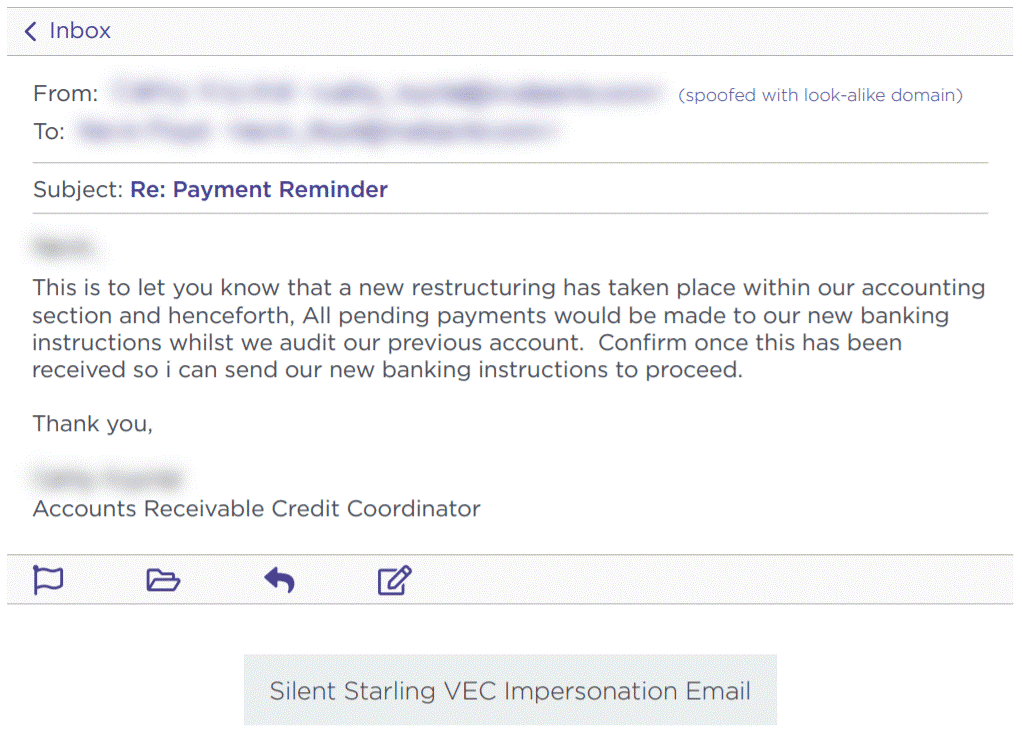
Another common type of phishing email is what is commonly known as ‘change of bank details fraud’ or ‘invoice fraud’. This involves a fraudster posing as a member of the accounts department of a supplier. The fraudster creates a convincing looking email and advises that their bank details have changed with the aim of getting you to make payments to the new account.
In order to avoid scams such as this, it is essential that you work on a basis of distrust when it comes to financial matters. If you are contacted out of the blue by a supplier to advise that their bank details have changed, call the customer on their official number (not the number in the email) and confirm this. If you receive an invoice that doesn’t seem quite right or that comes from a different email address, call the customer and check. It is better to be overly cautious than reckless – especially when bank details are involved.
So how can we avoid becoming a victim of these sorts of attacks?
Firstly, we suggest treating every email with a degree of suspicion. Think about the following:
- Is the sender’s email address correct? Often attackers use similar email addresses to legitimate senders so it is best to check this very carefully
- Were you expecting this message?
- Are there any ‘red flags’ such as spelling mistakes, incorrect information or suspicious attachments?
- Is there a request for payment or for you to sign in using your password?
- Does the message have a threatening tone? For example, does it advise that unless you take action immediately there will be severe consequences?
- Do you use the product which is mentioned?
- Is the email from someone you know and communicate with regularly?
When in doubt, it is always better to be safe than sorry. If the email purports to be from someone you know, call them and check that it is a legitimate message. If it appears to be from your bank or a government department, call them on the correct number and confirm (NOT the number in the email you have received, but the number from their official website).
Follow us to keep updated with all the latest IT news, tips, tricks and best practices.
References:
https://www.ncsc.gov.uk/guidance/phishing
https://it.sheridancollege.ca/service-catalogue/security/images/phishing-samples/amazon-phish.jpg
https://resources.infosecinstitute.com/category/enterprise/phishing/#gref
https://heimdalsecurity.com/blog/vendor-email-compromise-vec/
Header image credit – https://www.freepik.com
As a business, IT security should be your primary concern. Although passwords have been around since 1961, they can be one of the first steps in keeping your business safe but can often be the weakest link.
Password Policies and Procedures
Having a standard policy for passwords – e.g. Minimum character count, at least 1 capital letter, 1 number and 1 symbol – is a good start to improve this typically weak area.
All of this however will be inevitably in vain if you, as a company, do not have proper procedure in place to follow regarding passwords.
This could include for example:
- Not disclosing your password.
- Not leaving your password written on a document left lying around the office.
- Not left cached inside browser windows.
Having a set procedure in place for your staff to follow can be crucial in making sure your business stays safe and secure.
The impact of non-secure passwords
A weak or non-secure password can cause a plethora of issues for you as a business.
Your password is the key to accessing your accounts and your systems, especially on the cloud, which means a weak password is like leaving the key in a lock. Having the same password for multiple accounts across your business can be likened to that same key being able to open all the other doors.
Once those doors are open your business is vulnerable, this could be in the form of ransomware or data theft or a whole host of other issues that could plague your business.
These threats could cause business downtime leading to a loss of time and money whilst you try to fix the problem and recover from it, not to mention GDPR.
Password Managing Applications
A password manager is an application that both generates secure passwords and stores those passwords to be used later. All you need is to remember your 1 master password to access the application.
Advantages of these are:
- You only need to remember one secure password.
- You can then use large strong generated unmemorable passwords for every other service, as you don’t need to remember those.
- They can be auto filled to your website login boxes so you don’t even have to type them in making logins to websites almost immediate.
- Works across multiple devices. The phone APP and chrome browser extension work in tandem, so your passwords are all with you, wherever you go.
As an extra layer of security, you should turn on two factor authentication (2FA) which we will cover later. This would mean that to access your password management software you would need a code generated on your mobile phone app typically google authenticator or a variant of that to login.
What we recommend
Here at Bowe, we recommend our businesses follow a standard business procedure for passwords.
This standard procedure involves:
- Changing passwords at every agreed interval – 30 days recommended
- Having a minimum of 8 characters to a password, at least 2 numbers and including at least 1 special character within the password.
We encourage this to try and make sure all our partners are as secure as they can be and limit the risk of potential threats to their business.
If in doubt you can check your password on https://www.haveibeenpwned.com/passwords to see if your password is on a password breach list of approximately 555 million passwords. If it is, change it immediately. Password breach lists are used by hackers to attempt access to accounts. The is serviced by https and is ran by trusted security researcher Troy Hunt.
Two factor Authentication
Anytime two factor authentication is available we recommend you set it up. It is worth noting two factor authentication through SMS is not as secure as google authenticator 2FA due to the possibility of a sim swap attack. This involves someone persuading your mobile phone carrier to swap your mobile number to their new number with a story that they have got a new phone. If they can convince the mobile phone carrier to change it, or by answering the security questions correctly, then your two factor codes will go to the attacker allowing them to reset your password and gain access to your accounts.
For the highest security two factor authentication, we recommend using a Yubikey. These are USB devices which have a button on them for you to press when generating a code.
Biometric Authentication
You will have heard of Face ID and finger print scanning. These are a way of proving that you are you. These are a great way of adding additional layers of security if the option is available to the system.
Summary
There are many ways in this day and age to protect your online accounts from hackers and a multi layered approach is always best. If there are ways of adding extra security so you are not just relying on a password to gain access to systems, then those should be investigated.
Top Image Credit: Technology vector created by slidesgo – www.freepik.com

Our mission has always been about providing our clients with the innovative technological solutions they need to realise their business ambitions.
We have been delivering this service to businesses across the UK for the past 25 years – handling everything from hardware and business systems to phone networks and IT support.
As part of our ongoing commitment to finding the best technology solutions, We are now proud to be a trusted partner of Webexpenses.
Webexpenses is an award-winning system which uses an innovative cloud-based approach to transform the way that employee expenses are able to be managed and monitored.
Fighting expense fraud – more about Webexpenses
Webexpenses replaces slow and inefficient manual ways of working with a streamlined solution – automated processes, real-time tracking and integrated policy checks.
It provides finance teams with the kind of effective tools that needed to guard against the risks posed by inefficient and outdated methods of expense management.
A recent global study, commissioned by Webexpenses, found that 47 percent of workers admit to falsifying or exaggerating their expense claims.
Despite this, 86 percent said they had never had any of their expense claims challenged or declined by their company.
It’s a situation which helps to explain how expense fraud has become such an endemic within the business world – contributing to global losses of around $2.9 trillion each year.
To find out more about this and other solutions we have to help you with your business, just get in touch on 0191 214 1750 or click here for more ways to contact us
The UK attracted more than 2,200 new inward investment projects in 2016 to 2017 with more than 107,000 jobs across the country safeguarded or created, according to new figures.
Figures published by the Department for International Trade revealed that the UK attracted more foreign direct investment projects than ever before for the year.
With more than 2,200 projects recorded, the post-referendum figures show an increase of 2% on the previous year. The data also shows that 75,226 new jobs were created, and 32,672 safeguarded, amounting to over 2,000 jobs per week across the country.
Overall, the UK is the number one destination for inward investment in Europe, with the technology, renewable energy, life sciences and creative industries all seeing an increase in the number of projects.
International Trade Secretary, Dr Liam Fox, said: “Almost one year on since the EU referendum, the UK continues to attract record levels of inward investment and remains extremely attractive to foreign investors.”
We agree. Digital technology is playing its part every day and our clients are benefitting from the use of IT to develop new projects and improve the efficiency of existing ones.
Bowe Digital offers a range of IT solutions that can help businesses take advantage.
Call us on 0191 214 1750 or email info@bowe.co.uk to find out how.
Bowe Digital – we make I.T. happen
Three quarters of businesses expect to increase the number of high-skilled roles over the coming years, according to the 2017 CBI/Pearson Education and Skills Survey.
The survey of 344 companies highlighted that 62% are seeing strong competition for candidates with appropriate qualifications.
Asked about the impact of the introduction of the £2 billion apprenticeship levy, 58% of firms plan to increase apprentice programmes.
Josh Hardie, CBI Deputy Director-General, said: “Skills have to be the beating heart of the UK’s Industrial Strategy – it’s the best growth strategy a country can have. More high-skilled opportunities are good news for our future – and a sign we can make progress on productivity – but this is tempered by the growing urgency around skills shortages.”
We agree that skills development is crucial, including in the digital sector where we see plenty of opportunities for young talent. For our part, we will do all we can to develop talented people.
Bowe Digital offers a range of IT solutions that can help businesses take advantage.
Call us on 0191 214 1750 or email info@bowe.co.uk to find out how.
Bowe Digital – we make I.T. happen
Growth in the UK’s private sector slowed in the three months to June, according to the latest CBI Growth Indicator.
The survey of 762 respondents across the distribution, manufacturing and service sectors showed the balance of firms reporting a rise in output at +6%, compared with +13% in the three months to May 2017.
However, private sector firms expect growth to pick up over the next three months and we support that viewpoint. This is a time for calm heads.
The many companies we work with are expressing confidence that trading conditions, while challenging, do remain positive.
We are playing our part, offering a range of IT solutions that can help businesses take advantage of the digital revolution.
Call us on 0191 214 1750 or email info@bowe.co.uk to find out how.
Bowe Digital – we make I.T. happen
Twenty-four innovative agri-tech projects have been awarded a share of £16 million through the latest round of the Government’s Agri-Tech Catalyst programme.
The money will help the companies solve the world’s greatest food challenges, including the need to provide ultra-sensitive storage.
The UK is a world leader in the fast growing agri-tech sector and, as a company that supports businesses in the food industry, we applaud this investment in technology to make companies as efficient as possible.
We see digital technology playing its part every day and our clients are benefitting from the use of IT to develop new projects and improve the efficiency of existing ones.
Bowe Digital offers a range of IT solutions that can help businesses take advantage.
Call us on 0191 214 1750 or email info@bowe.co.uk to find out how.
Bowe Digital – we make I.T. happen
The Federation of Small Businesses is calling on the Government to ensure that all SMEs receive at least a basic level of broadband by the end of the Parliament.
Nearly half a million (480,000) small businesses cannot access superfast broadband, with 192,000 not even being able to access 10 Mbps and theFSB wants the Government to commit to a Universal Service Obligation (USO), guaranteeing a good service.
Mike Cherry, FSB National Chairman, said: “Too many small businesses are held back by poor broadband coverage and slow speeds.”
We agree – good broadband is crucial if companies are to take advantage of the digital revolution and the services that we offer.
Our IT support services use advanced remote monitoring and preventative maintenance technologies to keep infrastructure optimised. Issues can be identified, reported, and resolved in real time.
Call us on 0191 214 1750 or email info@bowe.co.uk to find out more.
Author – Be Everywhere