Microsoft has announced that it will be increasing its prices for Microsoft 365, Dynamics 365 and Power Platform SKUs from 1st of March 2022, as well as introducing a New Commerce Experience (NCE).
The changes to the commercial pricing for Microsoft 365, which are the first substantive pricing updates since Office 365 launched a decade ago, reflect the shift towards hybrid working and support the advances in Office 365 and Microsoft 365.
The New Commerce Experience, the NCE ‘Per Seat’ model, is a licensing model which is based on the number of ‘seats’/people who use the software. The aim of this approach is to reduce licensing complexity and provide flexibility for future growth. NCE per Seat will be available for Microsoft 365, Dynamics 365, and Power Platform SKUs with terms of 1 month, 1 year or 3 years.
1 month subscription
- Benefits – Useful for seasonal businesses or those with uncertain workforce patterns, the 1-month commitment offers flexibility.
- Term – One full month with no pro-rata refunds.
- Price – 20% higher than the 12 month subscription.
- Seat changes – Seats can be increased at any time. You cannot decrease the number of licenses/reduce your seat count during the subscription term.
12 month subscription
- Benefits – The 12-month term commitment allows you to secure a fixed cost for one year.
- Term – Twelve months with no pro-rata refunds.
- Price – In line with current pricing.
- Seat changes – Seats can be increased at any time. You cannot decrease the number of licenses/reduce your seat count during the subscription term.
36 month subscription
- Benefits – The 36-month term commitment allows you to secure a fixed cost for three years.
- Term – Thirty-six months with no pro-rata refunds.
- Price – In line with current pricing.
- Seat changes – Seats can be increased at any time. You cannot decrease the number of licenses/reduce your seat count during the subscription term.
Please note, Microsoft will not provide pro-rata refunds for the early termination of any subscription in NCE Per Seat outside of an initial 72-hour cancellation window.
What does this mean for you?
If you are a Microsoft 365 customer of Bowe Digital, a member of our team will be in touch with you to discuss the changes in more detail. In the meantime, if you have any concerns or questions about the changes, please contact us.
Bowe Digital will be closing from 1pm on the 24th December, 2021 until the 4th January, 2022.
We will be available for emergency calls on select days and times only, as detailed below:
- Monday, 27th Dec (Bank holiday) – Closed
- Tuesday, 28th Dec (Bank holiday) – Closed
- Wednesday, 29th Dec – 10.00am – 4.00pm
- Thursday, 30th Dec – 10.00am – 4.00pm
- Friday, 31st Dec (New Year’s Eve) – 10.00am – 1.00pm
- Monday, 3rd Jan (Bank holiday) – Closed
- Tuesday, 4th Jan – Normal hours resume
We hope you have a lovely Christmas and new year, and we look forward to working with you in 2022 and beyond.
Come and meet the Bowe Digital team at the North East Automotive Alliance Expo on the 30th September 2021 at the Beacon of Light, Sunderland.
We will be manning our own stand at the event, you can find us at A22, where our team of specialists will be on hand and happy to speak with you about our wide range of transformative IT solutions and services. This includes cloud solutions, hardware, networking, software, cyber security, and IT support services, to help your business increase productivity, improve performance, enhance connectivity, and reinforce security.
We are a proud member of the NEAA and have been providing friendly, professional, and reliable IT support services, predominantly to North East businesses, of all sizes and across a breadth of sectors for more than 25 years.
The NEAA provides an excellent platform to reconnect the region’s automotive sector, and its flagship exhibition is designed to bring together suppliers and technology providers face-to-face with the exemplar automotive community. The Expo will facilitate business and knowledge exchange right there on the show floor.
We’re looking forward to the Expo giving us a chance to meet fellow NEAA members and get in front of more North East businesses to discuss how we can support their advanced technology and IT requirements.
Get in touch to find out more about how we can support your business, or if you would like to come and speak to us at the Expo, you can sign up for a delegate pass here.
One of the downsides of being in a remote region in the world like the Australian outback or even in some rural villages is the slow speeds of internet where fibre hasn’t quite reached yet or isn’t economically viable to do so.
Elon Musk and Space X looks to solve all these issues with satellite internet constellation called Starlink.
What is Starlink?
The Starlink constellation will consist of thousands of small satellites in low Earth orbit, working in unison with ground transceivers.
The satellites can be used by you and me, military or even specialist research, allowing faster connections all over the world and in some of the most inhabitable environments where internet signal could prove to be a life saver. The cost of the decade-long project to design, build, and deploy the constellation was estimated by SpaceX in May 2018 to be at least US$10 billion.
As of September 2020, SpaceX was launching up to 60 satellites at a time, aiming to deploy 1,584 of the 260 kg (570 lb) spacecraft to provide near-global service by late 2021 or 2022.
Last month Space X confirmed Starlink is now available in parts of Wales, Scotland, Northern Ireland and Northern England,” which is in addition to existing service areas across Southern England.
As more and more satellites are launched, the areas which are currently hit, and miss will receive better connection and better signal.
How many satellites will Space X launch?
ITs reported that by 2024, there might be as many as 4,425 in operation, exploding to 12,000 around 2026.
How much does this space age internet cost then?
Customers typically pay £89 per month for the service itself, plus £54 for shipping and £439 for the kit (dish, router etc.). It may not be the cheapest but if you are suffering from exceptionally poor internet, it may be worth considering.
How fast is fast?
During beta, users can expect to see data speeds vary from 50Mb/s to 150Mb/s over the next several months as Starlink system is enhanced. There will also be brief periods of no connectivity at all, which is unfortunate but that should only be until a satellite becomes in range in low earth orbit.
As Space X launch more satellites, install more ground stations, and improve the networking software, data speed, latency and uptime will improve dramatically.
So, there you have it. Do you suffer from extremely poor broadband in a rural area? Would you pay £89 per month? Let us know in the comments.
What is Multi-factor Authentication (MFA)?
Multi-factor Authentication (MFA) is a security system in which to gain access to a specific resource you need to provide two or more forms of identification. Some examples of this may be entering your password in addition to either a pin code sent to your mobile device, an authentication app, a fingerprint or a security key.
The majority of security breaches are due to insecure passwords. MFA helps prevent this as with a username and password alone, an attacker will not be able to gain access to a secure system or resource. This is because although they may have compromised the username and password, they still lack the second factor required to gain access.
So why implement Multi-factor Authentication (MFA)?
- According to Microsoft, when you implement MFA your accounts are up to 99.9% less likely to be compromised
- Implementing MFA can be low cost, or even free, depending which service(s) you use
- MFA can give you peace of mind that your data is secure when being accessed from locations other than the office
- MFA is generally very easy to use
- Small businesses are increasingly being targeted by cyber criminals. MFA makes it much harder for them and is easily rolled out
- Users are already becoming accustomed to using MFA for things like online banking
MFA is highly recommended by IT Security professionals:
- Alex Weinert, Microsoft’s Group Program Manager for Identity Security and Protection says, “Your password (rules) don’t matter, but MFA does. Go turn on MFA if you haven’t.”
- Symantec have said that 80% of security breaches could be prevented by using MFA
- The National Centre for Cyber Security (NCSC) in the UK recommend the use of MFA
- We at Bowe Digital use MFA in order to access Microsoft 365, Webroot, our RMM service and more
In conclusion, implementing MFA is definitely a step you should take in order to protect your business. The benefits of implementing MFA outweigh the drawbacks and it is an easy way to improve your security.
Contact us today for advice on how you can enforce MFA and protect your company.
Due to the current Covid-19 pandemic, many of us are adjusting to a new normal of working from home. Whilst there are benefits to this, it can present a unique set of new challenges. One such challenge is how to effectively communicate and collaborate with our colleagues without being in the same office.
The good news is there is a huge range of software designed for this purpose to choose from. In this article, we will cover the four most prominent on the market today and examine the advantages and limitations of these.
1. Microsoft Teams
Part of the Microsoft 365 suite, Microsoft Teams is a communication and collaboration platform which replaces Skype for Business. Microsoft Teams combines workplace chat, video meetings, file storage and collaboration on files.
Advantages:
- Comes with Office 365 at no additional cost (depending on license)
- Instant messaging eliminates the need for long email chains
- Video calls with multiple colleagues at once
- Easy to implement and use
- File sharing and collaboration
- App integration
Limitations/Issues:
- Requires an Office 365 subscription
- Team set up and permissions can be complex
2. Zoom
Zoom is a cloud-based online meetings platform which has recently gained a lot of attention due to its ease of use and media coverage. Video conferencing, chat and business telephony services are their main offerings.
Advantages:
- Use of the video conferencing platform is completely free for up to 40 minutes with a maximum of 100 participants
- Sign up is not required for participants by default
- Easy to use and works on most devices
- Up to 1000 video participants on business plans with 49 video feeds on screen
- Screen sharing and annotation
- File sharing
Limitations/Issues:
- Information security professionals have raised concerns about Zoom’s data security and privacy practises
- “Zoom-bombing” – where unwanted users can enter a meeting and disrupt it if they find the meeting link
- Audio and video quality can deteriorate when large numbers of participants join a meeting
3. Slack
Slack is an instant messaging application to which has been around since 2013. It is relatively similar to Microsoft Teams in terms of its offerings.
Advantages:
- Ability to create channels to divide your teams and dedicate people to focused discussions and work
- Channels allow you to host video calls, chat separately within your own team and host virtual meetings
- File sharing between teams for collaboration
- Easy to use, simple design
- Automated actions and reminders
Limitations/issues:
- High volume of “urgent” messages
- Can be difficult to retrieve important information from a Slack chat
- Private channels cannot be changed to public if needed
- Can become expensive for larger companies
4. Google Meet
Available as a part of G Suite, Google Meet is Google’s enterprise video conferencing software. You can have a maximum of 250 participants on the enterprise license.
Advantages:
- Comes with G-suite at no extra cost
- Works in-browser on Google Chrome, Firefox, Microsoft Edge and Safari without installing any additional software or plugins
- Integrates with other meeting solutions
- Guests can join using a dial-in phone number in case of not having internet access
Limitations/Issues:
- Dashboard is not as clean as in some other meeting software
- No free option (you must have a G suite subscription to host meetings)
- No end-to-end encryption of video meetings
Our location feature is back this month and stopping off at the exquisite Wynyard Hall.
Steeped in history, this spectacular North East landmark commands centre stage when it comes to romantic destinations! Wynyard Hall (Wynyard Estate) started in journey in 1230 when the estate was leased to Sir Hugh de Chapell by King Edward 1.
Many families have owned the estate over the years, however, the hall as we know it today was not completed until 1846. Recent investment by Sir John Hall was the turning point which catapulted the hall to becoming a leading hotel destination for not only people within the North East but from all over the world.
The venue provides guests with the opportunity to indulge in a range of luxurious experiences including flavours in the dining rooms, complete relaxation with the range of spa treatments and romance with the outstanding wedding facilities.
Wynyard Hall Gardens are a location within a location. The stunning gardens and tea rooms provide visitors with the ability to escape day to day – it is like stepping into another world and with the addition of gorgeous homemade food, it really does make the perfect day out.
With the addition of the fabulous houses and development of Wynyard Village, the area has become a desirable place to live, work and play.
Corporate events are another aspect to Wynyard Hall with many exhibitions and conferences being held at the venue.
As a real bonus we are running a competition with Wynyard Hall where one lucky winner can enjoy afternoon tea for 2. We would love to know what celebrity you would take to afternoon tea – you can comment on our social media posts or email enquiries@bowe.co.uk with your answer. Keep an eye on our website for details of the date of the prize draw.
https://www.wynyardhall.co.uk/
Using Microsoft Excel is an excellent way to quickly generate calculations on your in-house data but things can get real frustrating real fast.
The first thing I learnt in Excel was to click on a cell, click the plus and click another cell and it totalled it up. Then I could drag it down the list, it was effortless, great I thought!
However, one thing I did initially struggle with on my first few days, was summing information down but then needing to calculate on something that always stayed in the same cell like a tax rate. This is where absolute cell references comes in!
F4 key / Using the dollar sign: $
This bit of information is key, if you are clicking on something which will always stay in the same cell, but everything else is in sequential cells moving down or across then press the F4 key. It will immediately insert dollars on to the cell in the formula which is a sign it has locked the reference with that cell.
For example: If you had a tax rate in cell A1 it would change it to $A$1 when you press F4.
Lets watch a video for a better understanding
First it will take you through relative cell references which we are all used to which is when excel fills the formula down for you. Then it will take you through absolute cell references from the 1m 45seconds in.
More Information
Using Microsoft Excel or other spreadsheet applications like Google Sheets can being great benefits to your day to day job allowing you to quickly organise information, sum up figures, and react to changing data patterns inside your business. Here at Bowe we are always just a phonecall away to help in situations where you might need some advice. Contact us here to see if we can help.
Phishing is a form of cyber attack where attackers attempt to trick users into doing ‘the wrong thing’, such as clicking a bad link that will download malware, or direct you to a website which may look identical to the original website, but may harbour spyware or be designed to collect your personal or financial information. In 2018 alone, phishing was responsible for $48,241,748 (£37,232,981.11) in losses.
Phishing can be conducted via a text message, social media, or by phone, but the term ‘phishing’ is mainly used to describe attacks that arrive by email. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive. Attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money.
Phishing emails can hit an organisation of any size and type. You might get caught up in a mass campaign (where the attacker is just looking to collect some new passwords or make some easy money), or it could be the first step in a targeted attack against your company, where the aim could be something much more specific, like the theft of sensitive data. In a targeted campaign, the attacker may use information about your employees or company to make their messages even more persuasive and realistic. This is usually referred to as spear phishing.
What does a Phishing email look like?

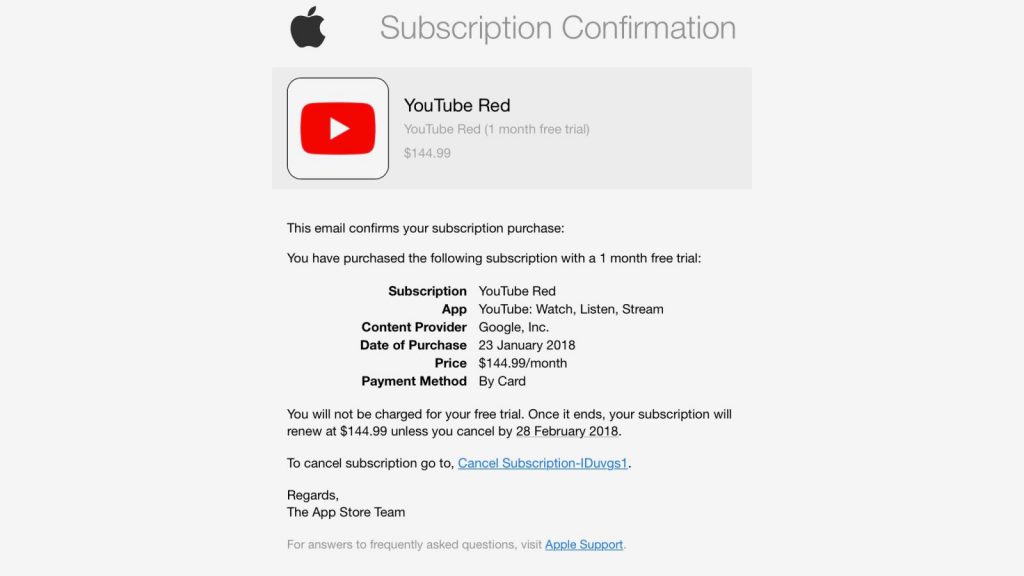
In this example above, we can see an email purporting to be from OneDrive, advising that there is a file which has been sent through to the user. Clicking the link in this email will result in malware being installed on your system. This is a common method of phishing where the attacker creates a message which would not look out of place amongst your normal work emails.
In this example above, we can see that an attacker has sent out an email attempting to get users to click the link and enter their Apple ID credentials. This may look convincing upon first glance, but as we look into it further, we can see that it is clearly not a genuine email. The combination of a non-apple email address being used to deliver the message, a generic and non-personalised greeting and the link pointing to a destination which has nothing to do with Apple are clear giveaways.
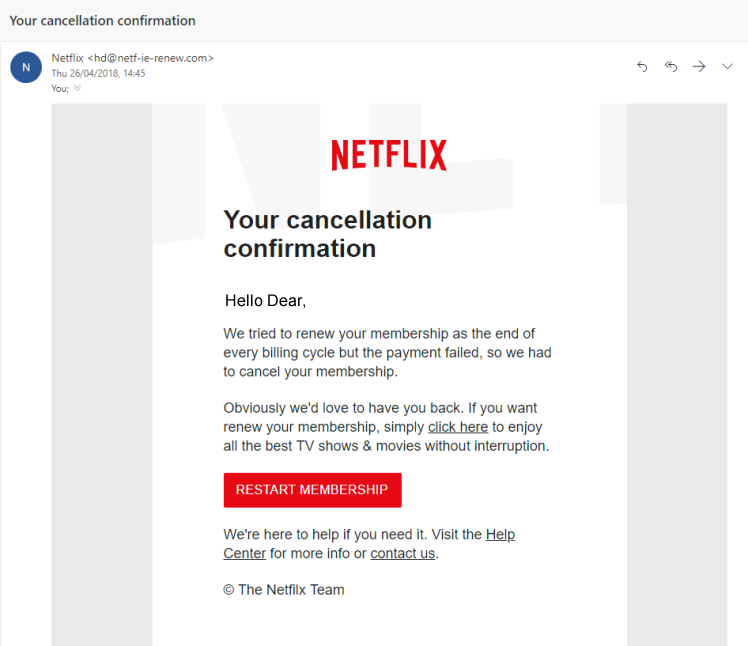
This example is one of the most common variants of a phishing email. On the surface, it looks pretty convincing – the branding is correct, the sign off seems correct and the look of the email seems legitimate apart from the recipient’s name. The only way you would be able to tell that this is not a legitimate email is to check the link in the email by hovering over it. In this case, it brings you to a false logon screen which is designed to steal your password. Another giveaway can be the email address that the message has originated from. Unless it is an @netflix.com (NOT @mailer.netflix.com or similar) email address, chances are it’s a phishing attempt.
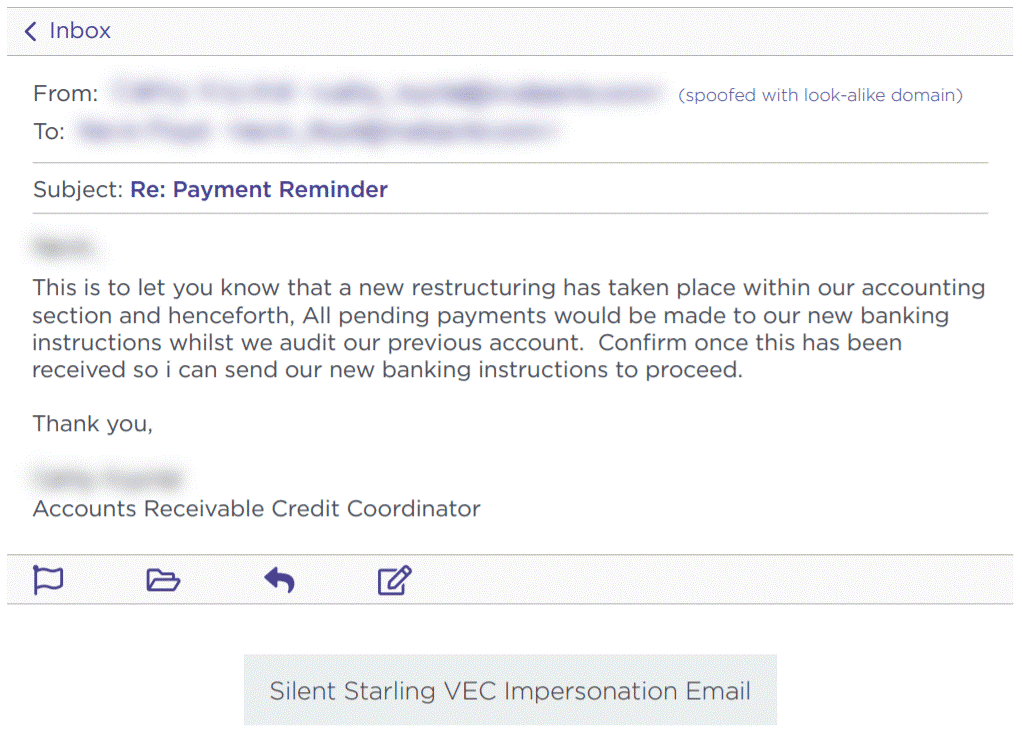
Another common type of phishing email is what is commonly known as ‘change of bank details fraud’ or ‘invoice fraud’. This involves a fraudster posing as a member of the accounts department of a supplier. The fraudster creates a convincing looking email and advises that their bank details have changed with the aim of getting you to make payments to the new account.
In order to avoid scams such as this, it is essential that you work on a basis of distrust when it comes to financial matters. If you are contacted out of the blue by a supplier to advise that their bank details have changed, call the customer on their official number (not the number in the email) and confirm this. If you receive an invoice that doesn’t seem quite right or that comes from a different email address, call the customer and check. It is better to be overly cautious than reckless – especially when bank details are involved.
So how can we avoid becoming a victim of these sorts of attacks?
Firstly, we suggest treating every email with a degree of suspicion. Think about the following:
- Is the sender’s email address correct? Often attackers use similar email addresses to legitimate senders so it is best to check this very carefully
- Were you expecting this message?
- Are there any ‘red flags’ such as spelling mistakes, incorrect information or suspicious attachments?
- Is there a request for payment or for you to sign in using your password?
- Does the message have a threatening tone? For example, does it advise that unless you take action immediately there will be severe consequences?
- Do you use the product which is mentioned?
- Is the email from someone you know and communicate with regularly?
When in doubt, it is always better to be safe than sorry. If the email purports to be from someone you know, call them and check that it is a legitimate message. If it appears to be from your bank or a government department, call them on the correct number and confirm (NOT the number in the email you have received, but the number from their official website).
Follow us to keep updated with all the latest IT news, tips, tricks and best practices.
References:
https://www.ncsc.gov.uk/guidance/phishing
https://it.sheridancollege.ca/service-catalogue/security/images/phishing-samples/amazon-phish.jpg
https://resources.infosecinstitute.com/category/enterprise/phishing/#gref
https://heimdalsecurity.com/blog/vendor-email-compromise-vec/
Header image credit – https://www.freepik.com
As a business, IT security should be your primary concern. Although passwords have been around since 1961, they can be one of the first steps in keeping your business safe but can often be the weakest link.
Password Policies and Procedures
Having a standard policy for passwords – e.g. Minimum character count, at least 1 capital letter, 1 number and 1 symbol – is a good start to improve this typically weak area.
All of this however will be inevitably in vain if you, as a company, do not have proper procedure in place to follow regarding passwords.
This could include for example:
- Not disclosing your password.
- Not leaving your password written on a document left lying around the office.
- Not left cached inside browser windows.
Having a set procedure in place for your staff to follow can be crucial in making sure your business stays safe and secure.
The impact of non-secure passwords
A weak or non-secure password can cause a plethora of issues for you as a business.
Your password is the key to accessing your accounts and your systems, especially on the cloud, which means a weak password is like leaving the key in a lock. Having the same password for multiple accounts across your business can be likened to that same key being able to open all the other doors.
Once those doors are open your business is vulnerable, this could be in the form of ransomware or data theft or a whole host of other issues that could plague your business.
These threats could cause business downtime leading to a loss of time and money whilst you try to fix the problem and recover from it, not to mention GDPR.
Password Managing Applications
A password manager is an application that both generates secure passwords and stores those passwords to be used later. All you need is to remember your 1 master password to access the application.
Advantages of these are:
- You only need to remember one secure password.
- You can then use large strong generated unmemorable passwords for every other service, as you don’t need to remember those.
- They can be auto filled to your website login boxes so you don’t even have to type them in making logins to websites almost immediate.
- Works across multiple devices. The phone APP and chrome browser extension work in tandem, so your passwords are all with you, wherever you go.
As an extra layer of security, you should turn on two factor authentication (2FA) which we will cover later. This would mean that to access your password management software you would need a code generated on your mobile phone app typically google authenticator or a variant of that to login.
What we recommend
Here at Bowe, we recommend our businesses follow a standard business procedure for passwords.
This standard procedure involves:
- Changing passwords at every agreed interval – 30 days recommended
- Having a minimum of 8 characters to a password, at least 2 numbers and including at least 1 special character within the password.
We encourage this to try and make sure all our partners are as secure as they can be and limit the risk of potential threats to their business.
If in doubt you can check your password on https://www.haveibeenpwned.com/passwords to see if your password is on a password breach list of approximately 555 million passwords. If it is, change it immediately. Password breach lists are used by hackers to attempt access to accounts. The is serviced by https and is ran by trusted security researcher Troy Hunt.
Two factor Authentication
Anytime two factor authentication is available we recommend you set it up. It is worth noting two factor authentication through SMS is not as secure as google authenticator 2FA due to the possibility of a sim swap attack. This involves someone persuading your mobile phone carrier to swap your mobile number to their new number with a story that they have got a new phone. If they can convince the mobile phone carrier to change it, or by answering the security questions correctly, then your two factor codes will go to the attacker allowing them to reset your password and gain access to your accounts.
For the highest security two factor authentication, we recommend using a Yubikey. These are USB devices which have a button on them for you to press when generating a code.
Biometric Authentication
You will have heard of Face ID and finger print scanning. These are a way of proving that you are you. These are a great way of adding additional layers of security if the option is available to the system.
Summary
There are many ways in this day and age to protect your online accounts from hackers and a multi layered approach is always best. If there are ways of adding extra security so you are not just relying on a password to gain access to systems, then those should be investigated.
Top Image Credit: Technology vector created by slidesgo – www.freepik.com