Phishing is a form of cyber attack where attackers attempt to trick users into doing ‘the wrong thing’, such as clicking a bad link that will download malware, or direct you to a website which may look identical to the original website, but may harbour spyware or be designed to collect your personal or financial information. In 2018 alone, phishing was responsible for $48,241,748 (£37,232,981.11) in losses.
Phishing can be conducted via a text message, social media, or by phone, but the term ‘phishing’ is mainly used to describe attacks that arrive by email. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive. Attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money.
Phishing emails can hit an organisation of any size and type. You might get caught up in a mass campaign (where the attacker is just looking to collect some new passwords or make some easy money), or it could be the first step in a targeted attack against your company, where the aim could be something much more specific, like the theft of sensitive data. In a targeted campaign, the attacker may use information about your employees or company to make their messages even more persuasive and realistic. This is usually referred to as spear phishing.
What does a Phishing email look like?

In this example above, we can see an email purporting to be from OneDrive, advising that there is a file which has been sent through to the user. Clicking the link in this email will result in malware being installed on your system. This is a common method of phishing where the attacker creates a message which would not look out of place amongst your normal work emails.
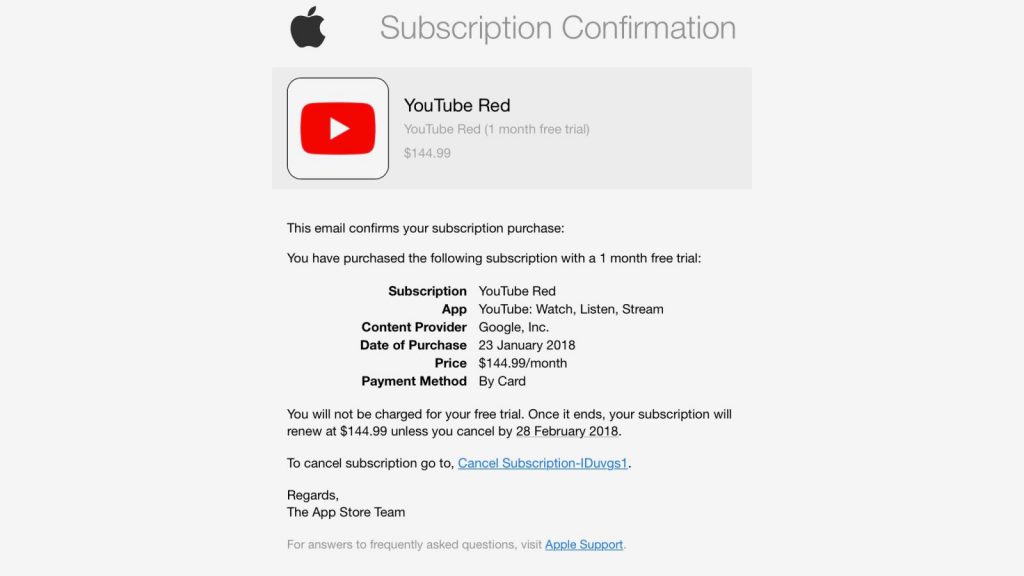
In this example above, we can see that an attacker has sent out an email attempting to get users to click the link and enter their Apple ID credentials. This may look convincing upon first glance, but as we look into it further, we can see that it is clearly not a genuine email. The combination of a non-apple email address being used to deliver the message, a generic and non-personalised greeting and the link pointing to a destination which has nothing to do with Apple are clear giveaways.
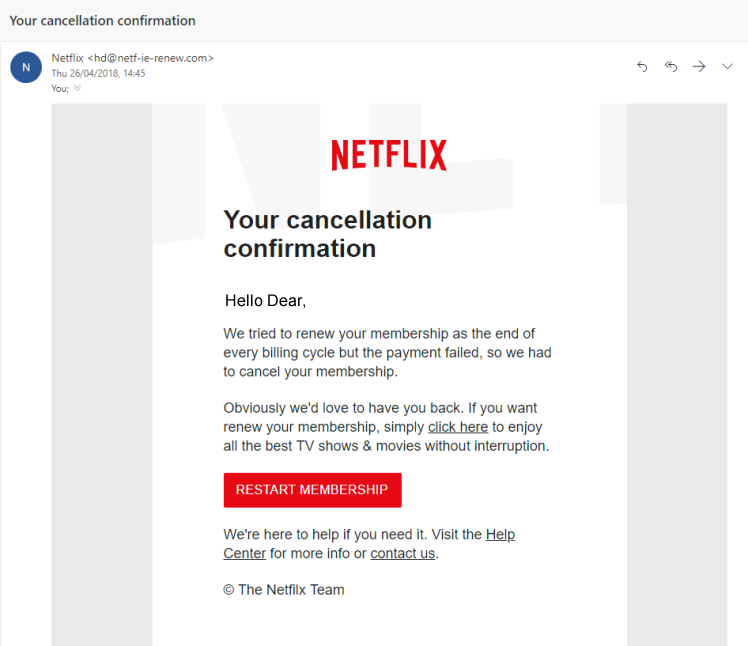
This example is one of the most common variants of a phishing email. On the surface, it looks pretty convincing – the branding is correct, the sign off seems correct and the look of the email seems legitimate apart from the recipient’s name. The only way you would be able to tell that this is not a legitimate email is to check the link in the email by hovering over it. In this case, it brings you to a false logon screen which is designed to steal your password. Another giveaway can be the email address that the message has originated from. Unless it is an @netflix.com (NOT @mailer.netflix.com or similar) email address, chances are it’s a phishing attempt.
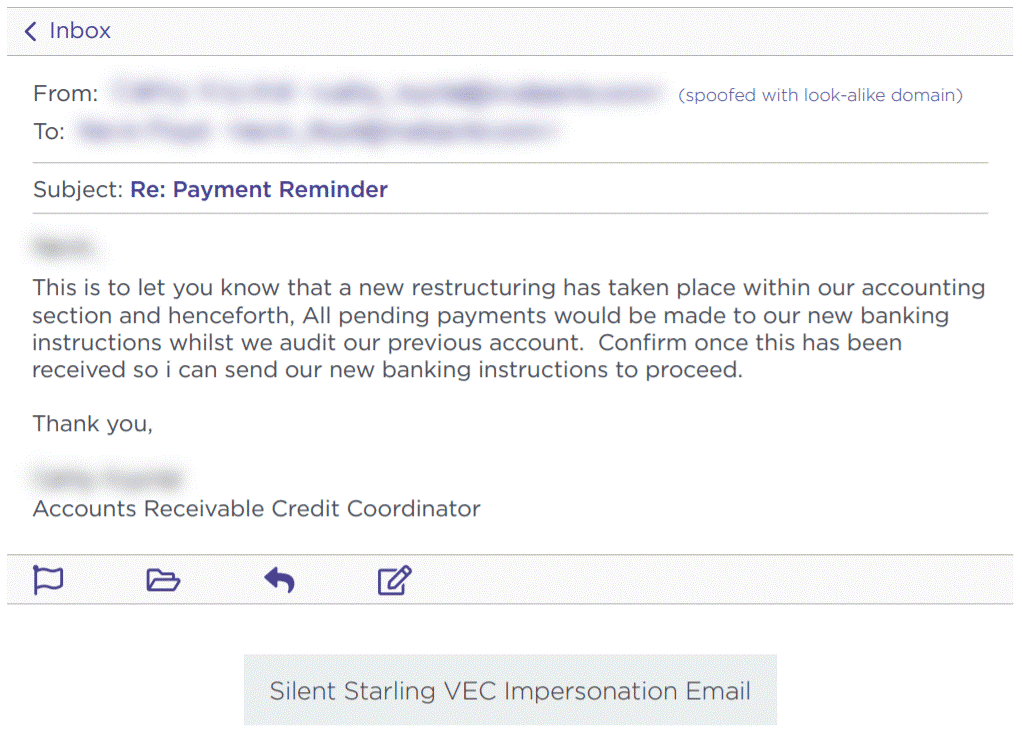
Another common type of phishing email is what is commonly known as ‘change of bank details fraud’ or ‘invoice fraud’. This involves a fraudster posing as a member of the accounts department of a supplier. The fraudster creates a convincing looking email and advises that their bank details have changed with the aim of getting you to make payments to the new account.
In order to avoid scams such as this, it is essential that you work on a basis of distrust when it comes to financial matters. If you are contacted out of the blue by a supplier to advise that their bank details have changed, call the customer on their official number (not the number in the email) and confirm this. If you receive an invoice that doesn’t seem quite right or that comes from a different email address, call the customer and check. It is better to be overly cautious than reckless – especially when bank details are involved.
So how can we avoid becoming a victim of these sorts of attacks?
Firstly, we suggest treating every email with a degree of suspicion. Think about the following:
- Is the sender’s email address correct? Often attackers use similar email addresses to legitimate senders so it is best to check this very carefully
- Were you expecting this message?
- Are there any ‘red flags’ such as spelling mistakes, incorrect information or suspicious attachments?
- Is there a request for payment or for you to sign in using your password?
- Does the message have a threatening tone? For example, does it advise that unless you take action immediately there will be severe consequences?
- Do you use the product which is mentioned?
- Is the email from someone you know and communicate with regularly?
When in doubt, it is always better to be safe than sorry. If the email purports to be from someone you know, call them and check that it is a legitimate message. If it appears to be from your bank or a government department, call them on the correct number and confirm (NOT the number in the email you have received, but the number from their official website).
Follow us to keep updated with all the latest IT news, tips, tricks and best practices.
References:
https://www.ncsc.gov.uk/guidance/phishing
https://it.sheridancollege.ca/service-catalogue/security/images/phishing-samples/amazon-phish.jpg
https://resources.infosecinstitute.com/category/enterprise/phishing/#gref
https://heimdalsecurity.com/blog/vendor-email-compromise-vec/