Chancellor Philip Hammond has announced that £1 billion will be invested in full-fibre broadband and trialling 5G networks from April 2017.
Bowe Digital welcomes the announcement, which is designed to make it easier for more companies to join the technological revolution.
The most successful businesses are the ones that harness the latest in technology to become more efficient and provide the best service to their customers.
In an age when every penny must count, forward-thinking companies realise that computer technologies allow them to ensure that their staff are directed to the best effect and that tasks that once took many hours can now be done quickly.
We offer a range of innovative IT solutions that can help companies improve their agility and efficiency.
Call us on 0191 214 1750 or email info@bowe.co.uk to find out how.
A new CBI survey of more than 8,000 businesses – supported by Deloitte and Hays – shows that 70% of respondents plan to increase or maintain their innovation spending following the vote to leave the EU.
Last year business invested almost £21bn on innovation, allowing British firms to develop cutting-edge products and services, attract global investment and expand internationally.
Carolyn Fairbairn, CBI Director-General, said: “Innovation is the nucleus of future economic and social development so it’s encouraging that seven out of ten firms will keep up – or even raise – their spending on new technologies and work practices to grow their business.
“As we prepare to depart the EU, this shows that firms are rolling up their sleeves and looking to make the best of Brexit.”
For many companies, innovation means investing in digital technology. Bowe Digital offers a range of IT solutions that can help companies improve their agility and efficiency.
Call us on 0191 214 1750 or email info@bowe.co.uk to find out how.
Bowe Digital – we make I.T. happen
The leader of a small businesses organisation has welcomed the recent launch of the Government’s strategy against cybercrime but warned that SMEs still need more protection.
The Federation of Small Businesses (FSB) said the National Cyber Security Strategy was welcome because small businesses are the victims of more than seven million cyber crimes a year, costing £5.26 billion annually.
FSB National Chairman Mike Cherry said:“When a small business is attacked, it can lead to weeks of delayed or lost orders, significant financial loss and damaged reputations. It’s an absolute necessity for businesses and Government to work together to increase the resilience of the small business community to help them get back on their feet after an attack.”
Bowe Digital can help protect your IT system against the latest cyber threats. Call us on 0191 214 1750 or email info@bowe.co.uk to find out how. Can you afford not to?
Bowe Digital – we make I.T. happen
The UK Government has launched a new Cyber Security Information Sharing Partnership (CISP), which aims to protect the nation from cyber attacks.
The partnership will bring together government experts, cyber-crime specialist and industry to share intelligence on the latest cyber security threats.
Francis Maude, the Cabinet Office Minister responsible for the Cyber Security Strategy, said when launching CISP: “We know that cyber attacks are happening on an industrial scale and businesses are by far the biggest victims of cyber crime in terms of industrial espionage and intellectual property theft with losses to the UK economy running into the billions of pounds annually.”
Bowe Digital can help protect your IT system against the latest cyber threats now.
Call us on 0191 214 1750 or email info@bowe.co.uk to find out how. Can you afford not to?
Bowe Digital – we make I.T. happen
Author – Be Everywhere
Understanding password strength and security
It’s becoming more and more common that when you sign up for any account online you see a password strength meter. They come in various shapes and sizes and are coded with varying restrictions that measure how easy your password would be to crack. Password strength meters work by measuring entropy, which shows the amount of time it would take for a hacker to get your password by using a brute force method. Also known as an “exhaustive key search” this process is basically a systematic attempt to guess all possible passwords until they find the correct one.
Exhaustive key search method for cracking passwords
Imagine you pop to the shops and lock your pushbike to the rails outside it using a padlock secured with a 4-digit code. If someone wants to steal your bike there is a finite number of possible ‘passwords’ that they can cycle through (pun intended) until they find the right one. The brute force method of stealing your bike would be to get a chainsaw and cut through the railing, but the brute force method of hacking your password would be to start by trying ‘0000’, then ‘0001’, then ‘0002’ and continue all the way up to ‘9999’. At some point the would-be thief/hacker would find the right password and they’d ride home on your bicycle.
Except, if your password is way up in the 8000s then it’s going to take the thief an age to try that many combination, and you’ll probably have finished your weekly shop by the time he’s even halfway through the possibilities.
In a theoretical universe where there are 100 thieves trying to get your bike, and they can all try a password combination simultaneously, then they’ll be away with your bike before you even pick up the shopping basket. One bike between 100 of them will be uncomfortable, mind you.
This multi-pronged attack is more relevant to computer based passwords, where it’s realistic that the computer can attempt a tonne of possible passwords in a very short amount of time. Password strength checkers like zxcvbn can show just how quickly a computer can guess your password. For the example password ‘fountain’ (admittedly not a very good one) a computer guessing 100 iterations per hour could crack the password in half a day. If it was guessing 10,000 passwords a second then it would be cracked in under a second.
This is why text only passwords are usually highly disregarded, and a lot of websites won’t even let you create an account with a text only password. Instead, you’re encouraged to increase the strength of your password with disguising factors like capitals, numbers, and symbols. On the ‘howsecureismypassword’ password checker the word ‘fountain’ was cracked instantly, but “Fountain123!” was cracked in 34 thousand years.
This measure of entropy is one way to see how quickly a computer could crack a password, but if we go back to the bike thief analogy, that thief knows that it’s far more likely that you’ve set your padlocks password to something memorable like ‘7777’ or ‘2468’, so he’s probably going to try a sequential, or palindromic pattern before he tries the brute force method of 0001, 0002, 0003. So don’t make your password 7777 or 1234 or 2468, and don’t make it 0001 either. If the thief really, really wants your bike then he might have done his research and found out when your birthday was – so don’t make the password your birthday either.
Common passwords
This mentality translates to computer passwords, too. Everyone knows that the most common password is ‘password’, yet people still use it. So a hacker will go straight to ‘password’ before he tries ‘aaaaaaaa’. On the internet you can find a list of the 10,000 most common passwords, and if hackers are trying to access your account they’ll cycle through these before they do anything else. A recent study showed that 30% of all passwords fall on the list of the 10,000 most common. Knowing the restrictions that websites have in place, hackers will also try variations of these common p@s5w0RD!S!S! that fall within the restrictions.
Combining all of this, we see that ‘Fountain123!’ isn’t actually as strong as that password checker suggested. The numbers are sequential, and the format of having the capital letter at the front and an exclamation mark at the end is a very standard way that people try to disguise passwords. It may have passed the brute force test, but a hacker with external knowledge would find it a lot easier to crack.
The strongest and safest passwords
So, after all that am I telling you that your password should be… *ahem*…ADF%$gwsdfgsdge5te45yFgxdfgsDFSDGdg54gsfgsdfgs2343£$?%”£$%”£?
No. Because you won’t remember that well enough to re-type it in the ‘repeat password’ validation, let alone be able to repeat it every time you visit the site. Instead, it’s suggested that passwords should actually be memorable ‘passphrases’ with all of the number, symbol, and case boxes ticked.
An example here would be that “Fountains123!” wasn’t actually a very strong password, but “FountainBikes!157” would take 93 trillion years to crack, and with passwords, longer is generally better. So by the https://howsecureismypassword.net/ password checker “PadlockThiefFountainBikes!157” is even better, and would take 4 undecillion years to crack.
For the record, depending on where you’re from, an undecillion is a 1 followed by either 36 or 66 zeroes. And there’s four of them. That’s a long time.
Sure, if a hacker has four undecillion computers to hack you with, then it’d only take them a year to get in. But in that case they must really, really want to read your emails – and just imagine the electricity bill.
PadlockThiefFountainBikes!157 passes the brute force test for password strength, as well as the human test. As a string of words it’s easy to remember but hard to crack because there’s no logical connection between them. The punctuation isn’t predictable and the number isn’t sequential or meaningful. It would take a hacker so long to get in that he’d just move on to the next guy long before he got anywhere near your information.
Follow this advice to choose the best passwords and stay safe online.
Author – James Norman
Website – http://blogs.fasthosts.co.uk/online-security/password-strength/
Sage Software, the financial accounting software vendor, has recently held its 2016 Sage Summit in Chicago. Over double the size of last year’s event in New Orleans, what did the event have to say about Sage’s future?
In many ways, not a lot. The headline speeches were largely around bringing in A-List celebrities (Gwyneth Paltrow, Zooey Deschanel, Ashton Kutcher, Sir Richard Branson) alongside inspirational people from the world of the Invictus Games and Sage’s own Sage Foundation. In amongst these sessions were dotted little snippets of product information.Was this a case of there not being any real news to give? Actually no – it was a clever strategy of getting Sage’s brand better known in the US where its problem is that many of its own customers still see it as Peachtree, and are not really aware of what else Sage has to offer.
Was this a case of there not being any real news to give? Actually no – it was a clever strategy of getting Sage’s brand better known in the US where its problem is that many of its own customers still see it as Peachtree, and are not really aware of what else Sage has to offer.
Last year was really a case of Sage CEO, Stephen Kelly, making a lot of noise to show that Sage had finally arrived at the cloud computing party. Sage Live and Sage One were front and centre, with lots of noise around the ‘c’ versions of Sage 50, 100 and 300. This was to try and head off the encroaching threat of web-native companies such as Xero, KashFlow and others – and it seems to have had a measure of success.
This year was far more a story of maturation and evolution. Cloud was presented as a given, although Kelly was still keen to ensure that everyone understood that Sage will not force any company to move from an on-premise version of its software to the cloud – ever. Sage will obviously make it more and more attractive for companies to make such a move – it will compensate its channel more for moving customers over; it will ensure that companies are aware of the extra capabilities that a globally shared platform can offer in B2B and B2C trading and so on.
The question is, will Sage ever start to purposefully not add specific functionality to its on-premise systems so as to make remaining on that platform not only less favourable but also less viable for its more conservative customers? Only time will tell.
So, what was new? New customer characterisations – out with SMB, mid-market and larger customers. It was stated that the customer base did not really identify with the terminology (something that Quocirca can also attest to). Instead, we now have start-up and scale-up segments. Nothing too startling about this – but it may well play well with companies that want to be seen as more dynamic than an “SMB”.
At the product level, Kelly was keen to focus on how he sees the need to continue to rationalise the product portfolio, bringing it down from the close to 300 products that were around what was effectively a global federation of different companies before he joined. This is being done by building out on an open API strategy, which decouples the front end (system of engagement) from the back end (system of record) so providing much greater flexibility going forward.
To the Cloud!
This also enables Sage to make a better play for building an app marketplace – it is introducing a new Integration Cloud that purportedly will allow code-less integration of Sage, public cloud and on-premise systems. If this works as promised, Sage will be able to be a cloud aggregator and broker.
This could, however, bring its own issues. Look at the majority of existing app marketplaces out there. It is worse than cable television – you think you know what you want, but finding it is difficult. You find something that you think is what you want, but it is badly put together and presented. You find just what you want, but it is in a different language. And so on.
Sage will need to be the honest broker in the middle, making the identification of what app is best for the user as easy as possible. It needs to empower the Sage community to rank and score apps to weed out those that are not up to the job. It needs to ensure that it doesn’t allow any third party to water down its stated commitment to joining its customers in a strategy of trust and security.
This could be further complicated based on some of the working examples Sage showed from its integrations with other products. One showed how it integrated into TomTom Fleet Manger, tracking an employee’s movements for mileage expenses and so on. It was said that this could also then be integrated into a time charging model, for example where a professional services employee enters a customer’s building and so can automatically starting charging the customer for their time.
This is great – as long as it all works and does not become seen as too ‘Big Brother’ by the employee. If it doesn’t work, identifying the root cause and remediating it could be difficult – and who gets it in the neck? Probably Sage.
The rise of the Bot.
The most interesting announcement, though, was something that was very innovative – not only for an accounting company but any company. Sage has brought in a very bright person, Kriti Sharma, to look at how artificial intelligence and machine learning can be brought into the world of financial systems. To this end, Sharma has developed Pegg, a bot. Somewhat of a mix of Cortana/Siri and TripIt, Pegg can take input from (at the moment) Slack and Facebook Messenger.
Why? Well, consider expenses – many companies such as SAP Concur (which owns TripIt) and KDS have worked on automating the expense process as much as possible – and yet users still struggle with it. By using a bot, it is possible to more quickly input the expense details in natural English, and Pegg will then deal with the intelligence required to sort it out and post it to the expense system.
Sharma is fully aware of the security and other issues that there could be around this, and also keenly aware of the possible power in a natural language interface to financial accounting processes that there is there as well. As such, she is ensuring that it is a case of small steps being taken to find out what users really want, how those requirements are dealt with and how security is managed along the entire process.
So, is Sage now safe? Not completely, but it is definitely not the turkey waiting to be stuffed. It still has plenty of progress to make, but as was pointed out, the majority of start-up and scale-up organisations around the globe are still using Microsoft Excel and other not-fit-for-purpose means of accounting.
The devil is in the detail – but Sage seems to be positioning itself as an interesting ingredient in an organisation’s business recipe.
Author – Clive Longbottom
Cloud computing, or cloud software, has become of the key trends in IT and business over the last couple of years. Cloud computing has been around for a while but with decent internet access now available nearly everywhere in the UK it is starting to come into its own. The basic principle is simple. Rather than buying expensive software, installing it on your computer and then having to back it up and update it regularly you simply pay a small fee to connect to a central server. The company providing the software will make sure it is up to date and backed up properly and you don’t need to install anything on your PC. This makes the whole process much easier.
One of the areas where we have seen a real benefit for new businesses is cloud based accountancy software. Traditional accountancy and bookkeeping software that you could install on your PC ran into hundreds of pounds. The new cloud-based programs, such as Sage One, run from a standard internet browser and cost £10 per month. However, the cost savings are not just in the cost of the software.
Most new businesses used to start out by recording their sales and expenses on an Excel spreadsheet. This works OK but it is relatively hard to run reports based on the Excel figures. Software such as Sage One allows you instantly see who owes you money and email them statements and invoices at the click of a button. This means you can easily stay on top of your cashflow and make sure your business is not losing money.
Most cloud based accountancy software also allows you to give you accountant access to your figures. They can log in to your accounts from their office and check what you are doing. In most cases they will be able to correct mistakes or, if necessary, download your numbers into their own software to prepare the end of year accounts. This saves a lot of time and has the potential to massively reduce your accountancy bills.
There are lots of benefits to using cloud-based software but the top 5 are:
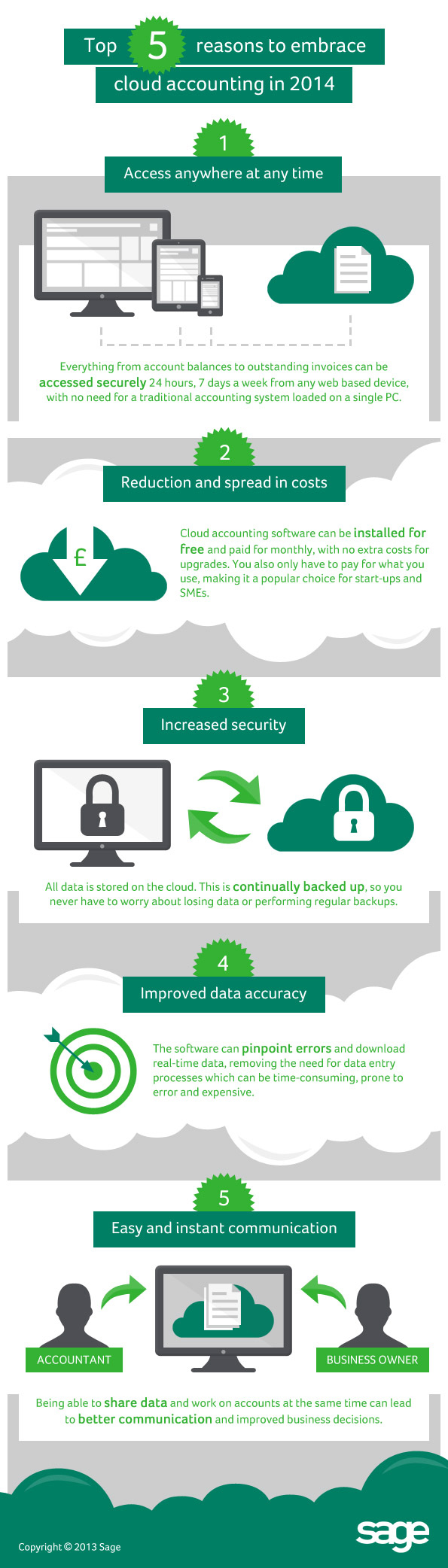
Author – Michael Summers
What is ‘Backing up data’?
Data backup is one of the most important areas of business IT and yet is also one of the most ignored. Backing up data making a copy of your most important and needed files; this can then be used if the original is lost or becomes corrupt.
Why you should backup?
Losing your business files can happen in a variety of ways, the common causes include your IT system failing physically, errors, theft or disasters like fire, flood and dropped mugs full of liquids! People also commonly save data to just one place, like ‘My Documents’ on your PC’s hard drive. Which means that if this data were to be changed or deleted it would take considerable time for IT support to restore it.
What should you backup?
Choosing which files is a good start to ensuring you have a copy of all your business’s important information. To help choose which files you should backup try thinking about what you would need to continue working if your PC were to be stolen/damaged. For example clients address/telephone details, your account information, important documents.
Another question to ask yourself when choosing which data to backup is “How long has it taken me to collate all this information and what would happen to the business if I couldn’t get it back once lost?” These are the key things that you should be thinking about.
What type of backup should I run?
There are many options to choose from, but the two moat popular options are an online or physical backup though a hard drive. Both have their advantages and are explained in detail in our most recent post, which you can read by clicking here.
If you have any more questions about backups or just IT in general, feel free to contact us and we’ll be happy to provide you with our IT support advice.
Website – http://www.pinfieldsit.co.uk/blog/Backing%20up%20Data
When it comes to upgrading your operating system on your laptop or PC the majority of organisations are happy to keep the system or application on the version they know and love. Most of us don’t like change as was seen with Microsoft’s removal of the Start Menu in Windows 8.
However, in the case of Content Management System (CMS) applications, there is a far greater risk to the business if it is not upgraded.
Let’s take Sitecore’s CMS as an example where a customer is still using Sitecore version 6.2; here are some of the risks associated with staying with this older version.
Internet Browsers:
Browsers like Firefox, Chrome and IE/Edge are constantly being updated, usually to remove security loopholes or unpopular abilities. This is great but it does mean your website will also require updating and tested with the latest versions. Quite often the CMS editor software will stop working with new browser versions or develop intermittent faults.
Sitecore support:
There is a Product Support Lifecycle that people should be aware of, for example, Mainstream Support for Version 6.6 ends December 31, 2015.
Underlying systems:
Sitecore and other CMS’s rely on underlying systems such as the Windows Server itself, SQL Server and the .NET Framework. These will also have support withdrawn from Microsoft; Windows 2003 server is a good example.
Migrating to newer versions of these underlying systems also means you will have no choice but to move to a newer version of your CMS as your old version may not run on Windows 2012, SQL 2014 etc.
Opportunities that come with upgrading your CMS to the latest version of Sitecore:
- Faster interface and improved search technology used throughout the editor
- Greater independence for the marketing team; more marketing features allows for the configuration and publication of personalised rules, content tests and engagement plans without the need for developer support
- Greater Cloud deployment efficiencies
- ‘Item Buckets’ (used to store large amounts of unstructured content) allows you to create any number of items in that bucket without being concerned about the underlying structure
- Keep up to date with online channels ensures faster and better ways of testing website and campaigns across numerous devices
- Keep up to date with developer tools
- Bulk actions on multiple items in Sitecore mean there is no longer the need to manually delete items one at a time.
Essentially, the longer an upgrade is left the longer and more painful it will be in the future. Moving from Sitecore 6.2 to Sitecore 7.2 currently needs many step upgrades – sometimes it’s better to install a new Sitecore instance and simply migrate the config and content. And, don’t forget third party modules and interfaces may no longer work on older versions.
The decision to upgrade your current CMS to the latest version may prove difficult, especially if it’s stable and running smoothly. However, there’s no getting away from the fact that moving to newer versions brings greater efficiencies and functional improvements – you’ll have to do it one day!
Author – Nigel King
Website – http://www.unified.co.uk/Blogs/September-2015-(1)/The-Risks-of-not-upgrading-your-CMS.aspx
Starting on July 28, Microsoft is making TPM 2.0 hardware-based security layer a requirement on Windows 10 smartphones, PCs and tablets.
Microsoft is rolling out a change in minimum hardware requirements for Windows 10 PCs and mobile devices, and expects hardware makers to comply in order to make their devices more secure.
Starting Thursday, PC makers should include a hardware-based security feature called TPM (Trusted Platform Module) 2.0 in Windows 10 PCs, smartphones and tablets.
Killing the password
Microsoft wants to kill passwords with a bio-metric authentication feature called Windows Hello, in which users can log into a PC via fingerprint, face or iris recognition. A TPM 2.0 chip is important to Windows Hello as it generates and stores the authentication keys in a secure area.
TPM 2.0 could also make two-factor authentication via Microsoft Passport—which could use bio-metric and pin-based authentication—a common feature in Windows 10 PCs. The Passport feature could be used to log into websites, applications and other services.
Microsoft has said TPM isn’t needed for Windows Hello, but recommends the security layer to protect bio-metric login data. TPM chips can be hard to hack, and do a better job protecting sensitive information than the software-based mechanisms that would otherwise be used to protect Windows Hello login data.
TPM definitely provides a security improvement in laptops, and is an excellent protection for encryption keys and other critically important data needed for authentication on the PC, said Kevin Murphy, vice president of operations at security company IOActive.
“Since it is hardware based rather than software based, the keys are not exposed to the PC memory. PC memory is a common venue for attackers to scrape intellectual property resident in the memory, which is usually the main purpose of the attack,” Murphy said.
However, using the TPM does not protect the encryption keys from being manipulated by an attacker. If an attacker “owns” the machine—for example by spoofing an authorized user—the TPM will answer any request as it normally would to the legitimate user.
“It will not know the difference. The advantage in this scenario is that the attack is limited to the current attack and cannot steal the keys for a future attack,” Murphy said.
It is possible to break TPM chips, but it would be a difficult attack, likely requiring a tremendous amount of skill, equipment, time, and investment, Murphy said.
Disk encryption system BitLocker already uses TPM to secure encryption keys. TPM is also used for secure software updates, to protect virtual machines and to authenticate smart cards. Intel’s vPro remote management service relies on TPM for authentication ahead of remote PC repairs.
Building TPM into everything
TPM 2.0 will be a minimum requirement on all Windows 10 devices except for developer boards like Raspberry Pi 3, which runs the lightweight Windows 10 IoT Core.
The security feature isn’t new; in fact it’s been available for years, mostly in business PCs. Many new PCs already have TPM 2.0, with an exception being low-cost PCs. Some Windows laptops have the older TPM 1.2 standard. But PC makers will now be expected to comply with Microsoft’s new hardware requirements and include TPM 2.0.
HP’s Elite X3 Windows 10 smartphone—based on Qualcomm’s latest Snapdragon 820 processor—already has TPM 2.0. The feature isn’t listed in Acer’s Liquid Jade Primo or Nokia Lumia models, which have older components.
Microsoft has been trying to drive hardware and software changes in PCs, some of which have been controversial. Upcoming PCs based on Intel’s Kaby Lake chips—which could be released in the third quarter—will support only Windows 10, not prior versions of the OS.
The software company earlier this year said it would support Windows 7 and 8.1 on Skylake devices until July 17, 2017, but extended that for one year after attracting criticism for trying to force an OS upgrade to Windows 10 on users.
TPM 2.0, a specification from Trusted Computing Group, was approved as an international standard by ISO/IEC (the International Organization for Standardization and the International Electrotechnical Commission) in June last year.
Author – Agam Shah




